最新要闻
- 男子疑因抽烟错过高铁不停拍车门 网友:怨不得别人
- 热点!40岁985硕士求职被怼不招大妈 求职者:感觉是歧视
- 报道:效仿微软XGP:Meta为Quest准备订阅制服务
- 每日短讯:健身猪一只最高能卖8万元:看完再也不配说胖得像猪了
- 环球百事通!联想小新Pro 16 2023酷睿独显版预售:7299元起 可选RTX4050
- 环球即时看!年度优秀员工评语简短(年度优秀员工评语)
- 世界动态:京东百亿补贴大杀器亮剑后 尚“无人伤亡”
- 奥斯卡影帝陨落“烂片之王” 凯奇:不愿加入漫威宇宙
- 信阳农专
- 动态:3.8节大促:腾讯视频、QQ、绿钻、B站、百度网盘会员五折起
- 看点:钢琴弹出的声音怎么这么好听啊?离不开这四大件!
- 我国多地将体验超前温暖:郑州要破29℃ 但秋裤还不能脱
- 环球速看:当下最完美全面屏!京东方宣布独家供应努比亚Z50 Ultra
- 丧心病狂!这些人利用AI声音冒充亲人诈骗1100万美元
- 快看点丨8个月宝宝像打冷颤一样头抖_婴儿偶尔腿打颤正常吗
- 被批恶俗烂梗 鸡你太美商标无一注册成功:超20枚被判无效
广告
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
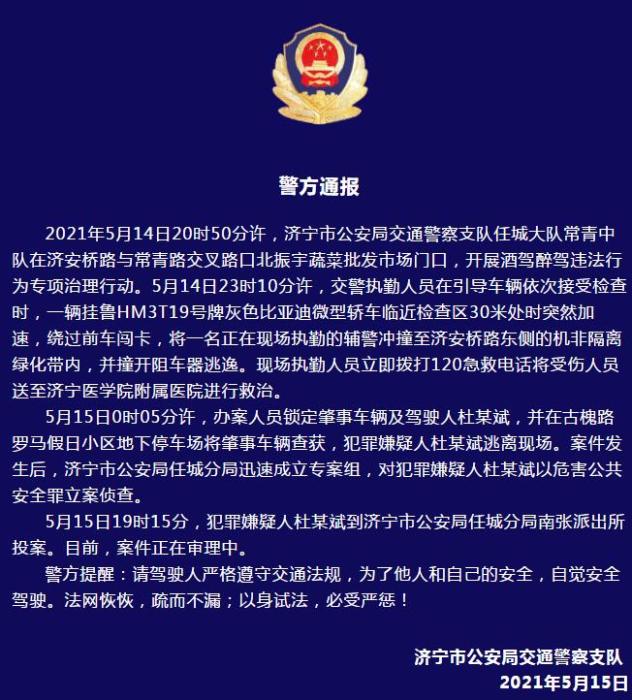
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
环球速讯:思科防火墙5506-x基础
防火墙的基本命令
查看防火墙的接口配置 show interface ip brief #这里和以往路由器和交换机不同 (sh ip interface brief)
查看路由:show route
 (资料图片仅供参考)
(资料图片仅供参考)
默认策略
高安全级别到低安全级别的流量是放行的
低安全级别到高安全级别的流量是拒绝的
配置inside区和outside区
ciscoasa>en ciscoasa#config t ciscoasa(config)#hostname ASA2 ASA2(config)#int g1/1 ASA2(config-if)#nameif inside ASA2(config-if)# security-level 100 //5505-X防火墙只要配置上inside区,默认安全级别就是100 ASA2(config-if)#ip address 192.168.4.2 255.255.255.0en
不同区域之间的互通配置
tips:首先设置接口端口区域,通过设置acl策略并将access-group作用域interface 区域中
ciscoasa(config)#interface gigabitEthernet 1/1ciscoasa(config-if)#ip address 200.1.1.1 255.255.255.0ciscoasa(config-if)#no shutdownciscoasa(config-if)#nameif insideINFO: Security level for “inside” set to 100 by default.ciscoasa(config-if)#security-level 0ciscoasa(config)#interface gigabitEthernet 1/2ciscoasa(config-if)#ip address 201.1.1.1 255.255.255.0ciscoasa(config-if)#no shutdownciscoasa(config-if)#nameif outsideINFO: Security level for “outside” set to 0 by default.ciscoasa(config)#interface gigabitEthernet 1/3ciscoasa(config-if)#ip address 203.1.1.1 255.255.255.0ciscoasa(config-if)#no shutdownciscoasa(config)#interface gigabitEthernet 1/3ciscoasa(config-if)#nameif dmzINFO: Security level for “dmz” set to 0 by default.ciscoasa(config)#route inside 200.1.1.0 255.255.255.0 200.1.1.2 #静态路由就自行添加了ciscoasa(config)#route outside 202.1.1.0 255.255.255.0 201.1.1.2ciscoasa(config)#route dmz 204.1.1.0 255.255.255.0 203.1.1.2ciscoasa(config)#access-list 101 extended permit ip any any //允许ip tcp icmp协议通过ciscoasa(config)#access-list 101 extended permit tcp any anyciscoasa(config)#access-list 101 extended permit icmp any anyciscoasa(config)#access-group 101 in interface dmz //在每个端口的出入方向进行acl部署ciscoasa(config)#access-group 101 out interface dmzciscoasa(config)#access-group 101 in interface insideciscoasa(config)#access-group 101 out interface insideciscoasa(config)#access-group 101 in interface outsideciscoasa(config)#access-group 101 out interface outside
配置asa的telnet和ssh
telnet配置
tips: 最低安全级别的接口不支持telnet 例如outside
ciscoasa(config)#telnet ?configure mode commands/options: WORD The IP address of the host and/or network authorized to login to the system X:X:X:X::X/<0-128> IPv6 address/prefix authorized to login to the system timeout Configure telnet idle timeoutciscoasa(config)#telnet 172.16.10.0 255.255.255.0 inside #设置telnet的区域和网段ciscoasa(config)#username lisen password miller #本地账户ciscoasa(config)#aaa authciscoasa(config)#aaa authentication ? #进行本地验证configure mode commands/options: ssh SSH telnet Telnetciscoasa(config)#aaa authentication telnet ?configure mode commands/options: console Specify this keyword to identify a server group for administrative authenticationciscoasa(config)#aaa authentication telnet console ?configure mode commands/options: LOCAL Predefined server tag for AAA protocol "local"ciscoasa(config)#aaa authentication telnet console LOCAL
ssh配置
asa#conf tasa(config)#hostname asa #配置主机名asa(config)#domain-name chinaskills.cn #配置域名信息asa(config)#crypto key generate ? asa(config)#crypto key generate rsa modulus 1024 #配置rsa的密钥长度WARNING: You have a RSA keypair already defined named.Do you really want to replace them? [yes/no]: yesKeypair generation process begin. Please wait...asa(config)#ssh timeout 1 #配置过期时间asa(config)#aaa authentication ssh console loasa(config)#aaa authentication ssh console loCAL #配置ssh本地登录asa(config)#username chian password P@ssword!23 #配置本地账户密码 asa(config)#ssh 10.1.1.0 255.255.255.0 inside #放行能够ssh的网段
ASA版本9.x SSH和Telnet在内部和外部接口配置示例 (cisco.com)
思科基于Cisco PT模拟器的防火墙配置实验案例详解_专业认证_IT专业知识_脚本之家 (jb51.net)
关键词:
-

-

-

-

第126篇: 异步函数(async和await)
环球速讯:思科防火墙5506-x基础
男子疑因抽烟错过高铁不停拍车门 网友:怨不得别人
热点!40岁985硕士求职被怼不招大妈 求职者:感觉是歧视
【LeetCode回溯算法#01】图解组合问题
报道:效仿微软XGP:Meta为Quest准备订阅制服务
每日短讯:健身猪一只最高能卖8万元:看完再也不配说胖得像猪了
环球百事通!联想小新Pro 16 2023酷睿独显版预售:7299元起 可选RTX4050
环球即时看!年度优秀员工评语简短(年度优秀员工评语)
[NOIP2017 普及组] 棋盘
AspNet Core MVC项目接入AdminLTE
世界动态:京东百亿补贴大杀器亮剑后 尚“无人伤亡”
奥斯卡影帝陨落“烂片之王” 凯奇:不愿加入漫威宇宙
信阳农专
精准管控|AIRIOT数字油库智能化解决方案
今日热门!k8s对外服务之Ingress
开发中用到的配置文本文件
当前通讯!Python定制对象的独有特征
动态:3.8节大促:腾讯视频、QQ、绿钻、B站、百度网盘会员五折起
看点:钢琴弹出的声音怎么这么好听啊?离不开这四大件!
我国多地将体验超前温暖:郑州要破29℃ 但秋裤还不能脱
环球速看:当下最完美全面屏!京东方宣布独家供应努比亚Z50 Ultra
丧心病狂!这些人利用AI声音冒充亲人诈骗1100万美元
5步绘制高质量流程图
世界消息!朴素贝叶斯与Laplace平滑
一篇搞懂cookie和session
【环球速看料】生成你的自定义密码本Python
快看点丨8个月宝宝像打冷颤一样头抖_婴儿偶尔腿打颤正常吗
被批恶俗烂梗 鸡你太美商标无一注册成功:超20枚被判无效
即时看!AMD Yes!FSR 2.2插件已适用于虚幻引擎
环球焦点!V12自吸发动机+三电机!兰博基尼旗舰跑车动力信息公布:超千匹
天天即时看!招不到人!新加坡软件工程师月薪基本都超4.6万 跑不赢房租
微动态丨今晚打老虎!周杰伦用《赌侠2》梗回应周星驰喊话
当前快播:记一次影视cms黑盒CSRF->RCE
OpenYurt 在龙源 CNStack 云边协同项目的应用
当前资讯!注解:@RequiredArgsConstructor、 @Validated、 @Valid、 @Lazy
全球微动态丨MP 代码生成器工具类
焦点消息!2999元起!五菱羚羊智能电动自行车发布:新国标 200km续航
天猫超级红包开抢:今晚抢30万个6.8元天猫红包 最高3888元
观速讯丨育碧“壮士断腕”:将对欧洲工作室实施战略重组
天天热资讯!人民网评论:别让恶俗网络烂梗毒害孩子 散发恶臭气息
观速讯丨Win11强制要求的金身告破 TPM 2.0漏洞影响数十亿设备
天天头条:60% 程序员大呼:我要远程办公!
世界热消息:一篇文章带你了解折线图
焦点短讯!创建型-单例模式
世界要闻:18位身份证校验Python
【世界热闻】百度统计快速实现网站访问量的统计
环球速递!任长霞电视剧剧情
世界要闻:「全国两会跨省联动报道」一生·一世·一群鸟——黑颈鹤与贵州保护者刘广惠的故事
16+512GB杀到2799元 一加Ace 2V颠覆友商:便宜1000多
观热点:摄影小白也能瞬间变大师!努比亚Z50 Ultra视频评测:最完美的无孔全面屏
当前快报:杭州亚运倒计时200天!首批亚运电竞特许商品上线:史上首次
当前报道:首发749元 一加Buds Pro 2轻享版发布:丹拿联合调音
即时焦点:蔚来丹麦首座换电站上线:老外“跪”在地上观看
Linux常用的20个命令(上)
天天速递!全景剖析阿里云容器网络数据链路(六):ASM Istio
全球聚焦:gitee突然无法访问
【天天时快讯】自从用了 Stream,代码更简洁优雅了!
每日观察!拍了10多年星星!努比亚Z50 Ultra升级11大星空算法
今日看点:AI免费设计LOGO效果惊艳 雷军200万花早了
1.6L自吸最大功率99kW 2023款日产轩逸本月上市
焦点日报:一加Ace 2V首发主动增强式超级Wi-Fi:穿墙能力提升30%
全球快报:一加Ace 2V触控体验碾压iPhone 14 Pro Max:在安卓阵营中表现最佳
全球微动态丨为什么99%的程序员都做不好SQL优化?
当前通讯!跟老杜从零入门MyBatis到架构思维(一)MyBatis概述
告别数据开发中的人工审核!火山引擎 DataLeap 落地“自动校验开发规范”能力
每日播报!Markdown语法学习
赞美翡翠的优美句子有哪些?
【世界速看料】“APP刺客”倒逼厂商升级大内存、大存储!8+128根本不够用了
天天微速讯:一人改代码搞崩推特 马斯克气疯:全部重写!
天天观察:出演《狂飙》爆红!雷军晒“大嫂”高叶人像照:小米13徕卡镜头
全球短讯!若依项目部署详解
最新:python奇葩反爬-你是故意的还是不小心的
全球观焦点:(数据库系统概论|王珊)第十章数据库恢复技术-第四、五、六、七节:数据库恢复技术和数据库镜像
全球百事通!以图搜图实现
每日播报!四步教会你如何画好流程图?
每日快播:华昌集团
全球聚焦:你几点睡?全国熬夜最狠城市揭晓:广东最牛 干这些行业的熬夜最多
金俊秀为什么叫细亚俊秀?金俊秀个人简介资料
已考上大学的简短四字祝福语有哪些?祝福前途似锦的古诗词有哪些?
强迫性动作属抑郁症吗?强迫性动作的自我疗法有哪些?
天天热点评!嫌弃之余,百度的这些搜索技巧真得会!
环球热议:EF7数据库提供者的自定义值生成器
全球热议:Use CMake notes
ArrayList和LinkedList的区别
咬甲癖是心理疾病吗?咬甲癖怎么治疗?
皮肤剥离强迫症是什么?皮肤剥离强迫症怎么治疗?
中移动董事长喊话中小学必学编程:还有委员喊话取消英语主科学了没用 你支持谁?
【世界快播报】最受欢迎的豪华中大型SUV 新款宝马X5实车亮相:国产必卖爆
湖北省“最强9万元补贴”蔓延 云南东风本田抄作业:直补6万
热点在线丨比Dev渠道更“快”!微软为Windows新增Canary测试渠道
全球观热点:砸130亿元 日本又失败!新主力火箭发射后自毁 日本专家谈落后中国多少年
焦点!【ES三周年】Elasticsearch安全配置详解
时讯:【MRTK】修改 HoloLens 应用的默认系统设置
新动态:开心档之Python3 面向对象
面试官要你介绍项目,怎么说?
每日速读!git的使用(一篇非常好的文章)
【快播报】老杜带你从零入门MyBatis,学MyBatis看这篇就够了!
bt种子是什么意思?bt种子怎么变成文件?
怎么查询手机号的号主姓名?怎么查询手机号用了多少年?





