最新要闻
- 4月皮卡销量排名出炉 长城江淮大增 新能源有待突破|世界时快讯
- 世界之最大全100条_世界之最大全
- 大模型三大能力超越ChatGPT 千亿AI巨头科大讯飞否认做手机
- 大爷买二等座票带孙女坐一等座被赶 12306回应:不允许乱坐 全球热点
- 【焦点热闻】好莱坞编剧大罢工:GPT技术引发激烈争议
- 经典28定律?苹果在中国手机市场份额2成 赚走8成利润|每日简讯
- 电池只能充电500次?别太荒谬!收下这份真正的充电秘籍
- 【全球新要闻】摊主买彩票中2千多万激动砸摊位:称21人合买 明天就分钱
- 每日精选:惠普打印机禁用非原装墨盒:官方称是为用户安全考虑
- 当前焦点!地狱笑话?大学母亲节配图是《进击的巨人》
- 泥鳅汤做法_泥鳅汤的烹饪方法 环球实时
- 已在轨生活160多天 航天员费俊龙从太空发回对母亲的节日祝福
- 热播电视剧将本科写成大专 高校不干了 官方道歉|天天聚看点
- 【热闻】首发紫光展锐T750!海信悄然推出F70 Lite手机
- 迭部县气象台发布大风蓝色预警信号【2023-05-14】
- DIY技巧:微星B760主板13600K降压教程 CPU温度暴降25℃
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
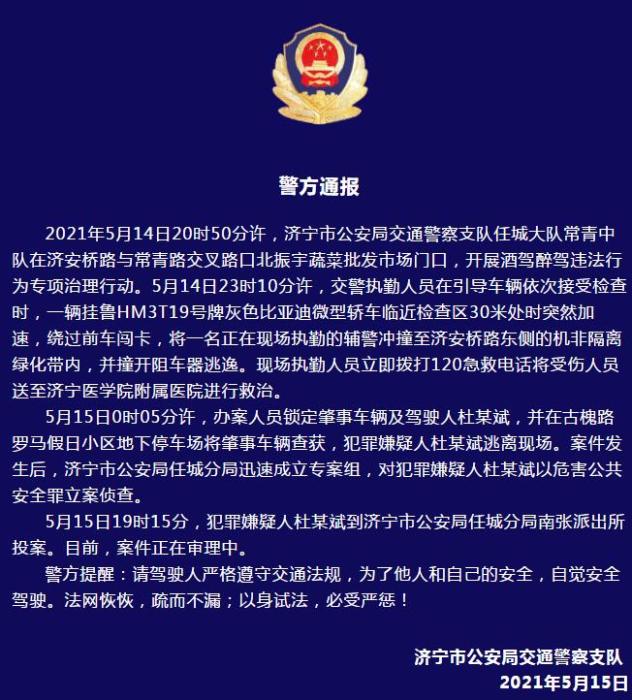
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
LitCTF crypto wp
Hex?Hex!(初级)
文件下载下来后得到:4c69744354467b746169313131636f6f6c6c616161217d直接16进制解码:
s ="4c69744354467b746169313131636f6f6c6c616161217d"print(bytes.fromhex(s))得到flag:LitCTF{tai111coollaaa!},换成NSSCTF{},下同
 (资料图)
(资料图)
梦想是红色的 (初级)
txt:自由友善公正公正敬业法治自由自由和谐平等自由自由公正法治诚信民主诚信自由自由诚信民主爱国友善平等诚信富强友善爱国自由诚信民主敬业爱国诚信民主友善爱国平等爱国爱国敬业敬业友善爱国公正敬业爱国敬业和谐文明诚信文明友善爱国自由诚信民主爱国爱国诚信和谐友善爱国自由友善平等爱国友善平等友善自由诚信自由平等爱国爱国敬业敬业友善爱国敬业敬业友善自由友善平等诚信自由法治诚信和谐
核心价值观编码直接在线解码
原来你也玩原神 (初级)
我靠!!。。。。咳咳咳,直接搜提瓦特大陆文字:![(https://img2023.cnblogs.com/blog/2698491/202305/2698491-20230514014343632-2137279192.png)]对照着下来就是flag:LitCTF{YUANLAINIYEWANYUANSHENWWW}
家人们!谁懂啊,RSA签到都不会 (初级)
from Crypto.Util.number import *from secret import flagm = bytes_to_long(flag)p = getPrime(512)q = getPrime(512)e = 65537n = p*qc = pow(m,e,n)print(f"p = {p}")print(f"q = {q}")print(f"c = {c}")"""p = 12567387145159119014524309071236701639759988903138784984758783651292440613056150667165602473478042486784826835732833001151645545259394365039352263846276073q = 12716692565364681652614824033831497167911028027478195947187437474380470205859949692107216740030921664273595734808349540612759651241456765149114895216695451c = 108691165922055382844520116328228845767222921196922506468663428855093343772017986225285637996980678749662049989519029385165514816621011058462841314243727826941569954125384522233795629521155389745713798246071907492365062512521474965012924607857440577856404307124237116387085337087671914959900909379028727767057"""import libnumimport gmpy2p = 12567387145159119014524309071236701639759988903138784984758783651292440613056150667165602473478042486784826835732833001151645545259394365039352263846276073q = 12716692565364681652614824033831497167911028027478195947187437474380470205859949692107216740030921664273595734808349540612759651241456765149114895216695451c = 108691165922055382844520116328228845767222921196922506468663428855093343772017986225285637996980678749662049989519029385165514816621011058462841314243727826941569954125384522233795629521155389745713798246071907492365062512521474965012924607857440577856404307124237116387085337087671914959900909379028727767057e = 65537n = p*qphi = (p-1)*(q-1)d = gmpy2.invert(e,phi)flag = pow(c,d,n)print(libnum.n2s(int(flag)))yafu (中级)
题目代码:
from Crypto.Util.number import *from secret import flagm = bytes_to_long(flag)n = 1for i in range(15): n *=getPrime(32)e = 65537c = pow(m,e,n)print(f"n = {n}")print(f"c = {c}")"""n = 15241208217768849887180010139590210767831431018204645415681695749294131435566140166245881287131522331092026252879324931622292179726764214435307c = 12608550100856399369399391849907846147170257754920996952259023159548789970041433744454761458030776176806265496305629236559551086998780836655717"""说了用yafu,然后如图其实也可以不用,factordb库挺好用的,直接生成列表:
from factordb.factordb import FactorDBf = FactorDB(15241208217768849887180010139590210767831431018204645415681695749294131435566140166245881287131522331092026252879324931622292179726764214435307)f.get_factor_list()f.connect()prime = f.get_factor_list()print(prime)e = 65537n = 15241208217768849887180010139590210767831431018204645415681695749294131435566140166245881287131522331092026252879324931622292179726764214435307c = 12608550100856399369399391849907846147170257754920996952259023159548789970041433744454761458030776176806265496305629236559551086998780836655717from functools import *a = 1phi = reduce(lambda a,b:a*(b-1),[1]+prime)d = pow(e,-1,phi)flag = pow(c,d,n)print(bytes.fromhex(hex(flag)[2:]))factordb(中级)
e = 65537n = 87924348264132406875276140514499937145050893665602592992418171647042491658461c = 87677652386897749300638591365341016390128692783949277305987828177045932576708额,和上道题一样,可以在线factordb.com分解,也可以用上道题代码,把值改一下即可,这里不多赘述
(校外)P_Leak
很简单的一道dp泄露,直接上代码:e = 65537n = 50612159190225619689404794427464916374543237300894011803225784470008992781409447214236779975896311093686413491163221778479739252804271270231391599602217675895446538524670610623369953168412236472302812808639218392319634397138871387898452935081756580084070333246950840091192420542761507705395568904875746222477dp =5892502924236878675675338970704766304539618343869489297045857272605067962848952532606770917225218534430490745895652561015493032055636004130931491316020329c =39257649468514605476432946851710016346016992413796229928386230062780829495844059368939749930876895443279723032641876662714088329296631207594999580050131450251288839714711436117326769029649419789323982613380617840218087161435260837263996287628129307328857086987521821533565738409794866606381789730458247531619for i in range(1, e): # 在范围(1,e)之间进行遍历 if (dp * e - 1) % i == 0: if n % (((dp * e - 1) // i) + 1) == 0: # 存在p,使得n能被p整除 p = ((dp * e - 1) // i) + 1 q = n // (((dp * e - 1) // i) + 1) phi = (q - 1) * (p - 1) # 欧拉定理 d = int(gp.invert(e, phi)) # 求模逆 m = pow(c, d, n) # 快速求幂取模运算print(m) # 10进制明文print("------------")print(hex(m)[2:]) # 16进制明文print("------------")print(bytes.fromhex(hex(m)[2:])) # 16进制转文本print("------------")print(libnum.n2s(m))md5的破解
from Crypto.Util.number import *from hashlib import md5from secret import flag#flag全是由小写字母及数字组成m=md5(flag).hexdigest()print(flag[:13]+flag[15:18]+flag[19:34]+flag[35:38])print(m)# b"LitCTF{md5can3derypt213thoughcrsh}"# 496603d6953a15846cd7cc476f146771根据代码内容,爆破md5
import stringimport hashliba="LitCTF{md5can??3de?rypt213thoughcr?sh}"b="496603d6953a15846cd7cc476f146771"dic1=string.digits+string.ascii_lowercase+string.ascii_uppercasefor i1 in dic1:for i2 in dic1:for i3 in dic1:for i4 in dic1:bb = "LitCTF{md5can" + i1 + i2 + "3de" + i3+ "rypt213thoughcr" + i4 +"sh}"aa = hashlib.md5(bb.encode("utf-8"))bbb = aa.hexdigest()if bbb == b:print(i1, i2, i3,i4)print("LitCTF{md5can" + i1 + i2 + "3de" + i3+ "rypt213thoughcr" + i4 +"sh}")e的学问
题目代码
from Crypto.Util.number import *m=bytes_to_long(b"xxxxxx")p=getPrime(256)q=getPrime(256)e=74n=p*qc=pow(m,e,n)print("p=",p)print("q=",q)print("c=",c)#p= 86053582917386343422567174764040471033234388106968488834872953625339458483149#q= 72031998384560188060716696553519973198388628004850270102102972862328770104493#c= 3939634105073614197573473825268995321781553470182462454724181094897309933627076266632153551522332244941496491385911139566998817961371516587764621395810123代码如下:
#sage环境运行p= 86053582917386343422567174764040471033234388106968488834872953625339458483149q= 72031998384560188060716696553519973198388628004850270102102972862328770104493c=3939634105073614197573473825268995321781553470182462454724181094897309933627076266632153551522332244941496491385911139566998817961371516587764621395810123N=p*qe=74phi=(p-1)*(q-1)d = pow(e//2,-1,phi)C = pow(c,d,N)P.=PolynomialRing(Zmod(p),implementation="NTL")f=a^2-Cmps=f.monic().roots()P.=PolynomialRing(Zmod(q),implementation="NTL")g=a^2-Cmqs=g.monic().roots()for mpp in mps: x=mpp[0] for mqq in mqs: y=mqq[0] solution = hex(CRT_list([int(x), int(y)], [p, q]))[2:] if len(solution) % 2 == 0: print(bytes.fromhex(solution))我测你vva
题目java代码如下:
public class Encrypto{ public static void main(String[] args) { String flag=""; int cipher; char[] arr; arr=flag.toCharArray(); for(int i=0; i上面的程序是一个简单加密算法的 Java 实现。该程序接受一个字符串输入,标志,并根据字符串中字符的索引是奇数还是偶数通过添加或减去一个值来加密它。然后将加密的字符串打印到控制台。
加密后的字符串存储在变量cipher中,其值为HYEQJvPZ~X@+Bp。要解密字符串,您可以根据每个字符在字符串中的索引,通过减去或添加相同的值来反转加密过程。以下是解密函数的示例实现:
def decrypt(cipher): result = [] for i in range(len(cipher)): shift = i if i % 2 == 0 else -i result.append(chr(ord(cipher[i]) - shift)) return "".join(result)encrypted = "HYEQJvPZ~X@+Bp"decrypted = decrypt(encrypted)print(decrypted)The same common divisor (高级)
from Crypto.Util.number import *m=bytes_to_long(b"xxxxxx")e=65537p=getPrime(1024)q1=getPrime(1024)q2=getPrime(1024)n1=p*q1n2=p*q2c1=pow(m,e,n1)c2=pow(m,e,n2)n3=n1^n2print("n1=",n1)print("n3=",n3)print("c1=",c1)print("c2=",c2)#n1= 9852079772293301283705208653824307027320071498525390578148444258198605733768947108049676831872672654449631852459503049139275329796717506126689710613873813880735666507857022786447784753088176997374711523987152412069255685005264853118880922539048290400078105858759506186417678959028622484823376958194324034590514104266608644398160457382895380141070373685334979803658172378382884352616985632157233900719194944197689860219335238499593658894630966428723660931647038577670614850305719449893199713589368780231046895222526070730152875112477675102652862254926169713030701937231206405968412044029177246460558028793385980934233#n3= 4940268030889181135441311597961813780480775970170156650560367030148383674257975796516865571557828263935532335958510269356443566533284856608454193676600884849913964971291145182724888816164723930966472329604608512023988191536173112847915884014445539739070437180314205284883149421228744714989392788108329929896637182055266508625177260492776962915873036873839946591259443753924970795669864031580632650140641456386202636466624658715315856453572441182758855085077441336516178544978457053552156714181607801760605521338788424464551796638531143900048375037218585999440622490119344971822707261432953755569507740550277088437182#c1= 7066425618980522033304943700150361912772559890076173881522840300333719222157667104461410726444725540513601550570478331917063911791020088865705346188662290524599499769112250751103647749860198318955619903728724860941709527724500004142950768744200491448875522031555564384426372047270359602780292587644737898593450148108629904854675417943165292922990980758572264063039172969633878015560735737699147707712154627358077477591293746136250207139049702201052305840453700782016480965369600667516646007546442708862429431724013679189842300429421340122052682391471347471758814138218632022564279296594279507382548264409296929401260#c2= 854668035897095127498890630660344701894030345838998465420605524714323454298819946231147930930739944351187708040037822108105697983018529921300277486094149269105712677374751164879455815185393395371001495146490416978221501351569800028842842393448555836910486037183218754013655794027528039329299851644787006463456162952383099752894635657833907958930587328480492546831654755627949756658554724024525108575961076341962292900510328611128404001877137799465932130220386963518903892403159969133882215092783063943679288192557384595152566356483424061922742307738886179947575613661171671781544283180451958232826666741028590085269一道简单的广播攻击:给了一个e,和多组的n,c。这些nc还都是一个明文m,通过对不同的n进行gcd()算法,求出最大公约数,(即p)求出P了,就能求出q,进而求出d, 解出明文m
import gmpy2import binasciie = 65537n1 = 9852079772293301283705208653824307027320071498525390578148444258198605733768947108049676831872672654449631852459503049139275329796717506126689710613873813880735666507857022786447784753088176997374711523987152412069255685005264853118880922539048290400078105858759506186417678959028622484823376958194324034590514104266608644398160457382895380141070373685334979803658172378382884352616985632157233900719194944197689860219335238499593658894630966428723660931647038577670614850305719449893199713589368780231046895222526070730152875112477675102652862254926169713030701937231206405968412044029177246460558028793385980934233c1 = 7066425618980522033304943700150361912772559890076173881522840300333719222157667104461410726444725540513601550570478331917063911791020088865705346188662290524599499769112250751103647749860198318955619903728724860941709527724500004142950768744200491448875522031555564384426372047270359602780292587644737898593450148108629904854675417943165292922990980758572264063039172969633878015560735737699147707712154627358077477591293746136250207139049702201052305840453700782016480965369600667516646007546442708862429431724013679189842300429421340122052682391471347471758814138218632022564279296594279507382548264409296929401260n2 = 13275392358603749049507302824073643158313511157306042129424622043169404438475070367199888792522735816696831092853554043588044629442339762181808939836068784930395387656511731023773900700005021564847480224798180592959510217158765133918150651706674329603149481255390797032771700235015269257730220757739489147426447858665350504461218790022992177725157756735193197648927044824616697206813752794351736481372892433605669363455272775767270738838271685683788851792503697508906872616175734362549442203442409947760416740297996886756365560632301306250478012961270642177511142736084877917270911656025730517314096773424314000497639c2 = 854668035897095127498890630660344701894030345838998465420605524714323454298819946231147930930739944351187708040037822108105697983018529921300277486094149269105712677374751164879455815185393395371001495146490416978221501351569800028842842393448555836910486037183218754013655794027528039329299851644787006463456162952383099752894635657833907958930587328480492546831654755627949756658554724024525108575961076341962292900510328611128404001877137799465932130220386963518903892403159969133882215092783063943679288192557384595152566356483424061922742307738886179947575613661171671781544283180451958232826666741028590085269p = gmpy2.gcd(n1,n2) # 欧几里得算法,p为两者的最大公约数q = n1 // pphi = (p-1)*(q-1)d = gmpy2.invert(e,phi)m = gmpy2.powmod(c1,d,n1)print(binascii.unhexlify(hex(m)[2:]))你是我的关键词(Keyworld) (初级),
txtx:IFRURC{X0S_YP3_JX_HBXV0PA}根据题目提示,为关键字密码,直接在现网站解密:密钥为大写:YOU
(校外)Is this only base?
SWZxWl=F=DQef0hlEiSUIVh9ESCcMFS9NF2NXFzM先栅栏数23解密,在base64解码,在凯撒密码解码
(校外)Virginia
下载下来是这:
Ysexj lrk rzmkses os wilj hhks joa rtsy xzmktye yt xuim ehgy joa ofsz blnz yz pohv tnjx fxtx yuzc dxjlmy fyd nzr tnjx fuw cegq! Orkfx wnfe yuz haty eo jwpas;lz wnjce etf wgse tu lz;bk bsaz dzu cfyt zt me,hjnaaxp yuz sabj znrd znk qtfk fyd usp cnfyck yz du fwl zmp tnnygy dzu cfyt zt oo.Sfj yuz sabj pnuzrh nfapospsy yz mgpp yuz dwkje,ettfgn ycigqd tu rlkk dzu yycotl,pnuzrh ytcrub eo qjpp etf harln,kszumm sovj eo sfve etf hguay? Gqhaex auz dzuxxpll ny ozmpry’xsokx.Tf etf fkjw tnfe iz mfrzx joa,ne pxtmahqj hawes zmp ozmpr vjcsus, eou.Yse nfapojdt uk aeuuwe jty’t tjneyxlroqj hgap tnj meyy zf kapreysitl;ehkd uuyy xaqj ehk rzsz tq ebjcyzmtnm ysaz hzmkx llusr tnjtr cfj.Hguaitjds rnps ltc tntde cmz cxd,ehuxp wnt suxy, ehuxp wnt sabj degwnhki,lnj ysoyj hhu mlvk yciki,qox tyle ysee hln guarkhtazj ehk nxpuweathp ol upovqp,wnt sabj eoahsej yseow wibjd.Luap bkltny bttn f dmoqp,gxths cneh g ptsy fyd ksos cneh g ypax.Yse hwtgnypsz kftawp woqw arblyy gp bgxpd us l fuwrozypn vfdt, etf cgs’e gu ty wkqw it qtfkzytoq joa qpt mt zf etfr vfdt lftlawps gso hkfctghsey.Bset dzu cjce htcn,etf wkwp cxdtnm fyd kapretye gwzuti joa bls yrtlosr.Loap yuzc lokp su ysaz bset dzu jnp,yuz"ce zmp otj hhu nd ssnwitl lnj jgexdznk fcoaso yuz ts iwjitl.Uwegxp skso tnnd mkxdamj eo zmzsk upovqp wnt xegs dosjehosr tu dzu,zt ehuxp wnt sabj eoahsej dzux qtfk ny otj hae tc attehkw,eo zmzsk bso sfve etf ssnwe cmpn etf rkfwle spej ne,tu ysoyj ehgy xaqj joa xpe zmp bxnrhzjc soip ol ysitld wnjy yuz lrk wparqj duby,tu ysoyj hhu dzu cfyt zt wez yses pyoc ysaz dzu guarkhtazj ehknc fxnpnjxsiv.Fyd ok joa izn’z, izn’z bzrxd,yozmtnm gld cnwl nfapks eo etf,yuz hirq uuyy xiyx zuz ty tnj zpvtctastte yz bxnrhzjy surpotj’d dgd hizm ehox xeyxlgk.Rj pgxdwuwo iy szt g wpgaqlr Ifpsgw aayxhoxi,lnj yse ksn frfr=[86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164] -Cgjdax维吉尼亚解码:Please send this message to those people who mean something to you,to those who have touched your life in one way or another,to those who make you smile when you really need it,to those that make you see the brighter side of things when you are really down,to those who you want to let them know that you appreciate their friendship.And if you don’t, don’t worry,nothing bad will happen to you,you will just miss out on the opportunity to brighten someone’s day with this message.My password is not a regular Caesar password,and the enc flag=[86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164] -Caesar知道是凯撒:flag=[86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164],与“LitCTF{”的ascii码作比较密文与明文之间,比如前六个数值与明文LitCTF的差距分别是-10,-11,-12.。。。代码如下:
flag=[86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164]j=-10for i in flag: print(chr(i + j), end="") j -= 1babyLCG
题目:
from Crypto.Util.number import *from secret import flagm = bytes_to_long(flag)bit_len = m.bit_length()a = getPrime(bit_len)b = getPrime(bit_len)p = getPrime(bit_len+1)seed = mresult = []for i in range(10): seed = (a*seed+b)%p result.append(seed)print(result)"""result = [699175025435513913222265085178805479192132631113784770123757454808149151697608216361550466652878, 193316257467202036043918706856603526262215679149886976392930192639917920593706895122296071643390, 1624937780477561769577140419364339298985292198464188802403816662221142156714021229977403603922943, 659236391930254891621938248429619132720452597526316230221895367798170380093631947248925278766506, 111407194162820942281872438978366964960570302720229611594374532025973998885554449685055172110829, 1415787594624585063605356859393351333923892058922987749824214311091742328340293435914830175796909, 655057648553921580727111809001898496375489870757705297406250204329094679858718932270475755075698, 1683427135823894785654993254138434580152093609545092045940376086714124324274044014654085676620851, 492953986125248558013838257810313149490245209968714980288031443714890115686764222999717055064509, 70048773361068060773257074705619791938224397526269544533030294499007242937089146507674570192265]"""简单的一道lcg,解题代码:
from Crypto.Util.number import *def gcd(a,b): if(b==0): return a else: return gcd(b,a%b)s = [699175025435513913222265085178805479192132631113784770123757454808149151697608216361550466652878, 193316257467202036043918706856603526262215679149886976392930192639917920593706895122296071643390, 1624937780477561769577140419364339298985292198464188802403816662221142156714021229977403603922943, 659236391930254891621938248429619132720452597526316230221895367798170380093631947248925278766506, 111407194162820942281872438978366964960570302720229611594374532025973998885554449685055172110829, 1415787594624585063605356859393351333923892058922987749824214311091742328340293435914830175796909, 655057648553921580727111809001898496375489870757705297406250204329094679858718932270475755075698, 1683427135823894785654993254138434580152093609545092045940376086714124324274044014654085676620851, 492953986125248558013838257810313149490245209968714980288031443714890115686764222999717055064509, 70048773361068060773257074705619791938224397526269544533030294499007242937089146507674570192265]t = []for i in range(9): t.append(s[i]-s[i-1])all_n = []for i in range(7): all_n.append(gcd((t[i+1]*t[i-1]-t[i]*t[i]), (t[i+2]*t[i]-t[i+1]*t[i+1])))MMI = lambda A, n,s=1,t=0,N=0: (n < 2 and t%N or MMI(n, A%n, t, s-A//n*t, N or n),-1)[n<1] #逆元计算for n in all_n: n=abs(n) if n==1: continue a=(s[2]-s[1])*MMI((s[1]-s[0]),n)%n ani=MMI(a,n) b=(s[1]-a*s[0])%n seed = (ani*(s[0]-b))%n plaintext=seed print(long_to_bytes(plaintext))easy_math (中级)
from Crypto.Util.number import *from secret import flagm = bytes_to_long(flag)e = 65537p = getPrime(512)q = getPrime(128)n = p*qhint = p**3-q**5c = pow(m,e,n)print(f"n = {n}")print(f"c = {c}")print(f"hint = {hint}")"""n = 2230791374046346835775433548641067593691369485828070649075162141394476183565187654365131822111419512477883295758461313983481545182887415447403634720326639070667688614534290859200753589300443797c = 2168563038335029902089976057856861885635845445863841607485310134441400500612435296818745930370268060353437465666224400129105788787423156958336380480503762222278722770240792709450637433509537280hint = 392490868359411675557103683163021977774935163924606169241731307258226973701652855448542714274348304997416149742779376023311152228735117186027560227613656229190807480010615064372521942836446425717660375242197759811804760170129768647414717571386950790115746414735411766002368288743086845078803312201707960465419405926186622999423245762570917629351110970429987377475979058821154568001902541710817731089463915930932142007312230897818177067675996751110894377356758932"""运sympy库解方程:
n = 2230791374046346835775433548641067593691369485828070649075162141394476183565187654365131822111419512477883295758461313983481545182887415447403634720326639070667688614534290859200753589300443797c = 2168563038335029902089976057856861885635845445863841607485310134441400500612435296818745930370268060353437465666224400129105788787423156958336380480503762222278722770240792709450637433509537280hint = 392490868359411675557103683163021977774935163924606169241731307258226973701652855448542714274348304997416149742779376023311152228735117186027560227613656229190807480010615064372521942836446425717660375242197759811804760170129768647414717571386950790115746414735411766002368288743086845078803312201707960465419405926186622999423245762570917629351110970429987377475979058821154568001902541710817731089463915930932142007312230897818177067675996751110894377356758932e = 65537import sympyimport libnumfrom Crypto.Util.number import *p,q = sympy.symbols("x,y")eq1 = p*q - 2230791374046346835775433548641067593691369485828070649075162141394476183565187654365131822111419512477883295758461313983481545182887415447403634720326639070667688614534290859200753589300443797eq2 = p**3-q**5-392490868359411675557103683163021977774935163924606169241731307258226973701652855448542714274348304997416149742779376023311152228735117186027560227613656229190807480010615064372521942836446425717660375242197759811804760170129768647414717571386950790115746414735411766002368288743086845078803312201707960465419405926186622999423245762570917629351110970429987377475979058821154568001902541710817731089463915930932142007312230897818177067675996751110894377356758932s = sympy.solve([eq1,eq2],[p,q])p = s[0][0]q = s[0][1]n=p*qfn=(p-1)*(q-1)d=inverse(e,fn)flag=pow(c,d,n)print("flag=",flag)print(libnum.n2s(int(flag)))隐晦的聊天记录
出题人:6c73d5240a948c86981bc294814d某不知名收件人:收到消息attack at dawn出题人:xxxxxxxxxxxxxxxxxxxxxxxxxxxx某不知名收件人:收到消息Monday or Thur已知出题人和收件人手中的密钥相同,请解出出题人第二次发送的密文呢(16进制,字母小写,解得的结果记得要加上LitCTF{}哦。)opt加密,直接异或:代码如下:
s = "6c73d5240a948c86981bc294814d"m1 = "attack at dawn"m2 = "Monday or Thur"# 将s和m1转换为二进制序列s_bin = bin(int(s, 16))[2:].zfill(len(s) * 4)m1_bin = "".join(format(ord(c), "08b") for c in m1)# 对二进制序列进行异或操作key_bin = ""for i in range(len(s_bin)): key_bin += str(int(s_bin[i]) ^ int(m1_bin[i]))# 将“Monday or Thur”转换为二进制序列m2_bin = "".join(format(ord(c), "08b") for c in m2)# 对二进制序列进行异或操作final_bin = ""for i in range(len(key_bin)): final_bin += str(int(key_bin[i]) ^ int(m2_bin[i]))# 将异或结果转换为字符串result = []for i in range(0, len(final_bin), 8): result.append (int(final_bin[i:i+8], 2))print(result)m = [64, 104, 207, 33, 8, 134, 140, 136, 158, 27, 242, 157, 131, 81]s = ""for i in m: s +=hex(int(i))[2:]print(s)#4068cf2108868c889e1bf29d8351Euler
题目如下:
from Crypto.Util.number import *from secret import flagm = bytes_to_long(flag)p = getPrime(512)q = getPrime(512)n = p*qc = pow(m,n-p-q+3,n)print(f"n = {n}")print(f"c = {c}")"""n = 115140122725890943990475192890188343698762004010330526468754961357872096040956340092062274481843042907652320664917728267982409212988849109825729150839069369465433531269728824368749655421846730162477193420534803525810831025762500375845466064264837531992986534097821734242082950392892529951104643690838773406549c = 406480424882876909664869928877322864482740577681292497936198951316587691545267772748204383995815523935005725558478033908575228532559165174398668885819826720515607326399097899572022020453298441"""c= m^(phi+2) mod n =m^2 * m^phi mod n又因为m^phi =1 mod nc = m^2 mod n解题代码:
import gmpy2from libnum import*n = 115140122725890943990475192890188343698762004010330526468754961357872096040956340092062274481843042907652320664917728267982409212988849109825729150839069369465433531269728824368749655421846730162477193420534803525810831025762500375845466064264837531992986534097821734242082950392892529951104643690838773406549c= 406480424882876909664869928877322864482740577681292497936198951316587691545267772748204383995815523935005725558478033908575228532559165174398668885819826720515607326399097899572022020453298441i = 0while 1: if(gmpy2.iroot(c+i*n,2)[1]==1): #开根号 print(gmpy2.iroot(c+i*n,2)) m = gmpy2.iroot(c+i*n,2)[0] break i=i+1print(n2s(int(m)))Where is P
题目:
from Crypto.Util.number import *m=bytes_to_long(b"XXXX")e=65537p=getPrime(1024)q=getPrime(1024)n=p*qprint(p)c=pow(m,e,n)P=p>>340print(P)a=pow(P,3,n)print("n=",n)print("c=",c)print("a=",a)#n= 24479907029118467064460793139240403258697681144532146836881997837526487637306591893357774423547391867013441147680031968367449693796015901951120514250935018725570026327610524687128709707340727799633444550317834481416507364804274266363478822257132586592232042108076935945436358397787891169163821061005102693505011197453089873909085170776511350713452580692963748763166981047023704528272230392479728897831538235554137129584665886878574314566549330671483636900134584707867654841021494106881794644469229030140144595938886437242375435914268001721437309283611088568191856208951867342004280893021653793820874747638264412653721#c= 6566517934961780069851397787369134601399136324586682773286046135297104713708615112015588908759927424841719937322574766875308296258325687730658550956691921018605724308665345526807393669538103819281108643141723589363068859617542807984954436567078438099854340705208503317269397632214274507740533638883597409138972287275965697689862321166613821995226000320597560745749780942467497435742492468670016480112957715214640939272457886646483560443432985954141177463448896521810457886108311082101521263110578485768091003174683555938678346359150123350656418123918738868598042533211541966786594006129134087145798672161268647536724#a= 22184346235325197613876257964606959796734210361241668065837491428527234174610482874427139453643569493268653377061231169173874401139203757698022691973395609028489121048788465356158531144787135876251872262389742175830840373281181905217510352227396545981674450409488394636498629147806808635157820030290630290808150235068140864601098322473572121965126109735529553247807211711005936042322910065304489093415276688746634951081501428768318098925390576594162098506572668709475140964400043947851427774550253257759990959997691631511262768785787474750441024242552456956598974533625095249106992723798354594261566983135394923063605rsa很典型的p高位泄露:代码如下:
import gmpy2 #先求Pfrom libnum import*n = 24479907029118467064460793139240403258697681144532146836881997837526487637306591893357774423547391867013441147680031968367449693796015901951120514250935018725570026327610524687128709707340727799633444550317834481416507364804274266363478822257132586592232042108076935945436358397787891169163821061005102693505011197453089873909085170776511350713452580692963748763166981047023704528272230392479728897831538235554137129584665886878574314566549330671483636900134584707867654841021494106881794644469229030140144595938886437242375435914268001721437309283611088568191856208951867342004280893021653793820874747638264412653721c= 22184346235325197613876257964606959796734210361241668065837491428527234174610482874427139453643569493268653377061231169173874401139203757698022691973395609028489121048788465356158531144787135876251872262389742175830840373281181905217510352227396545981674450409488394636498629147806808635157820030290630290808150235068140864601098322473572121965126109735529553247807211711005936042322910065304489093415276688746634951081501428768318098925390576594162098506572668709475140964400043947851427774550253257759990959997691631511262768785787474750441024242552456956598974533625095249106992723798354594261566983135394923063605i = 0while 1: if(gmpy2.iroot(c+i*n,3)[1]==1): #开根号 print(gmpy2.iroot(c+i*n,3)) break i=i+1#sagefrom sage.all import *n=24479907029118467064460793139240403258697681144532146836881997837526487637306591893357774423547391867013441147680031968367449693796015901951120514250935018725570026327610524687128709707340727799633444550317834481416507364804274266363478822257132586592232042108076935945436358397787891169163821061005102693505011197453089873909085170776511350713452580692963748763166981047023704528272230392479728897831538235554137129584665886878574314566549330671483636900134584707867654841021494106881794644469229030140144595938886437242375435914268001721437309283611088568191856208951867342004280893021653793820874747638264412653721P= 66302204855869216148926460265779698576660998574555407124043768605865908069722142097621926304390549253688814246272903647124801382742681337653915017783954290069842646020090511605930590064443141710086879668946#P为p去除0的剩余位e = 0x10001pbits = 1024kbits = pbits - P.nbits()print(P.nbits())P = P << kbitsPR. = PolynomialRing(Zmod(n))f = x + Proots = f.small_roots(X=2^kbits, beta=0.4)if roots: p = P+int(roots[0]) print("n= "+str(n)) print("p= "+str(p)) print("q= "+str(n//p)) baby_xor
from Crypto.Util.number import *from secret import flagm = bytes_to_long(flag)assert len(flag)==32p = getPrime(512)q = getPrime(512)n = p*qe = 65537c1 = p^mc2 = pow(m,e,n)print(f"n = {n}")print(f"c1 = {c1}")print(f"c2 = {c2}")"""n = 139167681803392690594490403105432649693546256181767408269202101512534988406137879788255103631885736461742577594980136624933914700779445704490217419248411578290305101891222576080645870988658334799437317221565839991979543660824098367011942169305111105129234902517835649895908656770416774539906212596072334423407c1 = 11201139662236758800406931253538295757259990870588609533820056210585752522925690049252488581929717556881067021381940083808024384402885422258545946243513996c2 = 112016152270171196606652761990170033221036025260883289104273504703557624964071464062375228351458191745141525003775876044271210498526920529385038130932141551598616579917681815276713386113932345056134302042399379895915706991873687943357627747262597883603999621939794450743982662393955266685255577026078256473601"""flag头已经知道了,异或一下能得到50bit,这样coppersmith就很好解了
#sage环境import gmpy2from Crypto.Util.number import *n = 139167681803392690594490403105432649693546256181767408269202101512534988406137879788255103631885736461742577594980136624933914700779445704490217419248411578290305101891222576080645870988658334799437317221565839991979543660824098367011942169305111105129234902517835649895908656770416774539906212596072334423407c1 = 11201139662236758800406931253538295757259990870588609533820056210585752522925690049252488581929717556881067021381940083808024384402885422258545946243513996c2 = 112016152270171196606652761990170033221036025260883289104273504703557624964071464062375228351458191745141525003775876044271210498526920529385038130932141551598616579917681815276713386113932345056134302042399379895915706991873687943357627747262597883603999621939794450743982662393955266685255577026078256473601m=0b1001100011010010111010001000011010101000100011001111011m=m<<200p=m^^c1p4=p>>220pbits = 512kbits = pbits - p4.nbits()p4 = p4 < = PolynomialRing(Zmod(n))f = x + p4x0 = f.small_roots(X=2^kbits, beta=0.4)[0]p = p4+x0assert n % p == 0q = n//int(p)assert p*q==ne = 65537phi = (q-1) * (p-1)d = inverse(e,-1,phi)m = pow(c2,d,n)print(m)print(long_to_bytes(m)) 关键词:
-

-

-
-

环球速看:EF命令行工具 migrate.exe 进行Code First更新数据库,6.3+使用ef6.exe
EF命令行工具migrate exe进行CodeFirst更新数据库,6 3+使用ef6 exe使用EF的CodeFirst迁移可以用于从Visual
来源: LitCTF crypto wp
世界速讯:监听容器中的文件系统事件
第139篇:微信小程序的登录流程|天天讯息
环球速看:EF命令行工具 migrate.exe 进行Code First更新数据库,6.3+使用ef6.exe
4月皮卡销量排名出炉 长城江淮大增 新能源有待突破|世界时快讯
20230514学习笔记——将代码提交到码云中 天天要闻
当前速递!【LeetCode字符串#extra】KMP巩固练习:旋转字符串、字符串轮转
世界之最大全100条_世界之最大全
大模型三大能力超越ChatGPT 千亿AI巨头科大讯飞否认做手机
大爷买二等座票带孙女坐一等座被赶 12306回应:不允许乱坐 全球热点
观点:一起来学rust|简单的mingrep
关于Kubernetes-v1.23.6-网络组件-calico的安装部署...|焦点快看
【焦点热闻】好莱坞编剧大罢工:GPT技术引发激烈争议
经典28定律?苹果在中国手机市场份额2成 赚走8成利润|每日简讯
电池只能充电500次?别太荒谬!收下这份真正的充电秘籍
【全球新要闻】摊主买彩票中2千多万激动砸摊位:称21人合买 明天就分钱
CentOS7搭建keepalived+DRBD+NFS高可用共享存储
每日精选:惠普打印机禁用非原装墨盒:官方称是为用户安全考虑
当前焦点!地狱笑话?大学母亲节配图是《进击的巨人》
泥鳅汤做法_泥鳅汤的烹饪方法 环球实时
已在轨生活160多天 航天员费俊龙从太空发回对母亲的节日祝福
热播电视剧将本科写成大专 高校不干了 官方道歉|天天聚看点
【热闻】首发紫光展锐T750!海信悄然推出F70 Lite手机
迭部县气象台发布大风蓝色预警信号【2023-05-14】
three.js 入门学习(二) 环球热资讯
DIY技巧:微星B760主板13600K降压教程 CPU温度暴降25℃
世界消息!专家称电动车要发展农村型号:支持反向充电 可增加收入
环球热门:1-2!“全校班”广州队又输了!3连败+开局5轮不胜,直冲降级区
基于SLAM系统建图仿真,完成定位仿真
天天观速讯丨安卓一年一迭代谷歌也累了:开始挤牙膏更新
女子把变心男友送的黄金卖了14万:没真心但有真金!自愿赠与或不用返还_天天快看
升级彩超5项:瑞慈体检套餐279元母亲节大促 今日热搜
久穿不易变形 放克220g宽松短袖29元大促
徐工四款新“国货之光”问世:百变狮王、自动灭火机器人 国产化率100% 世界观焦点
万胜智能: 关于使用部分闲置募集资金进行现金管理的进展公告
美团一面:Spring Cloud 如何构建动态线程池?
动态焦点:每天走路超这一步数 能大幅降低死亡率 上班族学起来
B站“离谱”专利获批:开车也能发弹幕了?|新要闻
热议:俄媒:泽连斯基拒绝教皇方济各调解俄乌提议
世界热议:我对IdentityServer4的初步了解
每日关注!JavaSE面试题【长期更新】
想玩《塞尔达传说:王国之泪》却不知道买哪款Switch?这篇选购攻略帮你避坑!
CPU散片学问大:碰见这两个型号千万别买|今日热搜
01-Linux命令和C语言基础|全球快讯
全球今亮点!西湖5平米商亭租金284万 每天约7780元引热议
母亲节 我来讲一个给妈妈换了“苹果全家桶”后的故事
首次发现!唾液含剧毒的五爪金龙现身云南:寿命长达150年
每日短讯:2023年5月14日融雪剂价格最新行情预测
国金证券:稳增长政策效果加速显现 居民消费修复延续性较强
D加密沦陷!黑客放出《生化危机4重制版》破解资源:好评如潮大作免费玩
AI起了反效果:4月微软Bing市场份额不升反降
特斯拉雨天高速失控!旋转、掉头、撞墙后 司机接着加速跑了
【报资讯】怀旧服磨刀石是什么专业制作的(怀旧服磨刀石)
前端语言串讲 | 青训营笔记
女子夜里打出租 全程直播监控!司机:不自信了_当前焦点
环球快资讯丨最后一道封印解除!ChatGPT重大升级 上线联网功能
检察院不批捕取保候审后还会收监吗|世界快播
女子旅游后高烧不退确诊“不死癌症” 医生:晒太阳是重要诱因
性能完全不达标 EPA报告:特斯拉4680电池能量密度比2170还低 当前观察
landrover是什么车多少钱一辆 landrover是什么车
Python学习之六_同时访问Oracle和Mysql的方法
上海张江全链条发力营造更优企业创新发展环境 今日快讯
放弃ZEKU自研芯片!OPPO张璇:产品生命周期软件维护不受影响_世界速读
江苏扬州:体育嘉年华嗨出狂欢味 百余场赛事活动贯穿全年-全球播资讯
曾为中国最大的汽车经销商 庞大集团濒临退市
今天母亲节 妈妈收到孩子送礼物时的反应让千万网友动容-全球关注
每日焦点!自称长相比较可爱28岁女副教授回应带梗招生:院方支持新表达方式
Windows 10操作系统绝唱了!终极正式版开始强制升级
天天快讯:保定市区养犬收费标准来了!登记500/300,年检200!
学系统集成项目管理工程师(中项)系列21b_整体管理(下)
母亲节今天到来!微信上线限时状态:感谢妈妈 天天动态
卖给中国人的车 连玻璃都减配? 全球快看点
大哥13 Ultra同款!小米13/Pro相机界面升级:变焦转盘调焦更方便
成都市验房公司_成都验房公司
Java Socket编程|环球聚看点
Ubuntu下通过Wine安装LTSpice 17.1.8_当前讯息
环球聚焦:讯飞输入法推出苹果 macOS 版,支持 10.15 及以上版本
当前快看:江苏女子到山东旅游买到的特产竟是戒尺:自己之前根本没有见过
环球速读:80、90后的青春记忆!《街霸》过气了吗?
iPhone用户被骗子盯上!三招轻松破解
北京一车主遇无接触事故被认定负全责 骑车人自己滑倒:网友吵翻
百万召回能解决单踏板电门当刹车?特斯拉回应:选择权给大家 误踩会提醒
莱州市永安路街道:帮办代办暖心解忧 架起为民服务“连心桥”
23岁网红用GPT-4复制自己,每月狂赚3500万 当前播报
Prompt learning 教学[案例篇]:文生文案例设定汇总,你可以扮演任意角色进行专业分析-天天即时
七孔大豆纤维夏被到手59元:牛奶般丝滑 亲肤透气 今日报
何炅录制芒果TV《向往的生活》:手机真我11 Pro+抢镜
安卓机皇!三星Galaxy S23 Ultra限量版上市:9488元 全球速读
淄博八大局知名麻辣串疑被房东赶走:老板回应双方还在商讨此事 世界视讯
厦门英才学校小学部第三套课间操_厦门英才学校小学部-天天热消息
今日快讯:算命奇想
就没有《猫和老鼠》还原不了的图!AI被锤爆了
热门:中性笔后面的神秘液体是什么?竟然大有讲究!
今日讯!德州驴出肉率_德州驴
小米13 Pro被低估了!雷军力荐:数码发烧友就选它|观点
通讯!00后女生旅游不忘给新手机开光 网友:你是懂开光的
焦点资讯:《暗黑4》遇上DLSS 3:最低帧猛增50%
迁移到 Gradle 7.x 使用 Version Catalogs 管理依赖
焦点热议:线段树
【LeetCode剑指offer#04】包含min函数的栈、栈的压入、弹出序列(辅助栈的应用)





