最新要闻
- 世界热讯:method怎么读音_method怎么读
- 899元 小米高端路由器7000开售:全2.5G网口、自研三频拓展
- 首款天玑9200+旗舰稳了!iQOO Neo 8 Pro现身谷歌支持列表|全球快讯
- 薄如原子的人工神经元面世:可处理光电信号 天天观速讯
- 奔驰提车当天出故障 要拆变速箱!博主:建议车主坐车头直播
- 印度一双层轮船因超载发生倾覆事故 现场视频曝光
- 强弱开始模糊中超竞争更加激烈-天天热文
- 环球热资讯!炭火炉子烤肉好吃还是电炉子烤的好吃?
- GPS侧目!北斗“女神”徐颖:我们追求毫米级甚至更小的精度_观天下
- 当前信息:金价又“狂飙”!全球第二大金矿商CEO透露:还押注了另一金属
- 环球实时:梦幻联动?马斯克公开赞同李想对于自动驾驶的理念
- 天津出台强降雨应急处置机制:规范处置程序 明确9项环节
- 【速看料】一季度西安居民人均可支配收入比上年同期实际增长5.4%
- iPhone 14令人失望!五星好评率暴降:苹果十年口碑瞬间崩塌
- 安卓最强5G Soc!联发科天玑9200+明天发:跑分一骑绝尘
- ob什么意思女生_ob什么意思
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
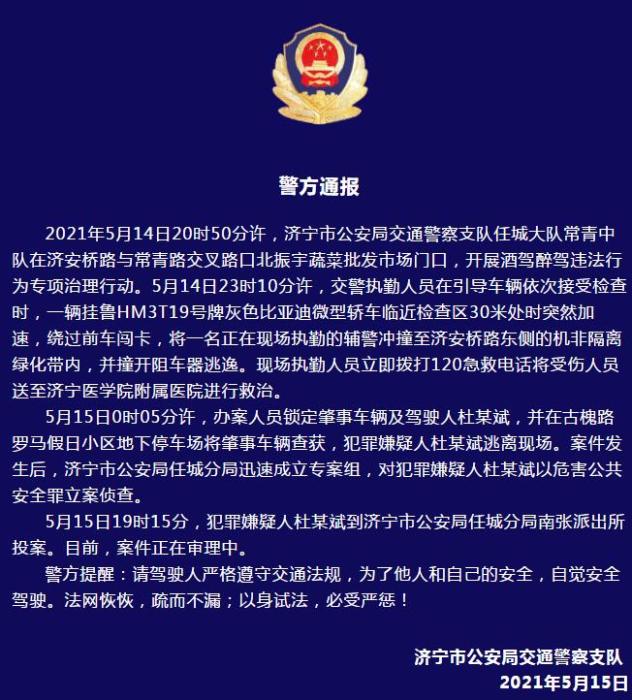
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
环球头条:Grafana 系列-统一展示-4-AWS Cloudwatch 数据源
系列文章
- Grafana 系列文章
AWS Cloudwatch 数据源
对于 AWS Cloudwatch, 主要在于 3 种不同的认证方式:
 (资料图片)
(资料图片)
- AWS SDK Default
- IAM Role
- AK&SK
- Credentials file
现在推荐的是使用 IAM Role 的认证方式,避免了密钥泄露的风险。
但是特别要注意的是,要读取 CloudWatch 指标和 EC2 标签 (tags)、实例、区域和告警,你必须通过 IAM 授予 Grafana 权限。你可以将这些权限附加到你在 AWS 认证中配置的 IAM role 或 IAM 用户。
IAM policy 示例如下:
Metrics-only:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AllowReadingMetricsFromCloudWatch", "Effect": "Allow", "Action": [ "cloudwatch:DescribeAlarmsForMetric", "cloudwatch:DescribeAlarmHistory", "cloudwatch:DescribeAlarms", "cloudwatch:ListMetrics", "cloudwatch:GetMetricData", "cloudwatch:GetInsightRuleReport" ], "Resource": "*" }, { "Sid": "AllowReadingTagsInstancesRegionsFromEC2", "Effect": "Allow", "Action": ["ec2:DescribeTags", "ec2:DescribeInstances", "ec2:DescribeRegions"], "Resource": "*" }, { "Sid": "AllowReadingResourcesForTags", "Effect": "Allow", "Action": "tag:GetResources", "Resource": "*" } ]}Logs-only:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AllowReadingLogsFromCloudWatch", "Effect": "Allow", "Action": [ "logs:DescribeLogGroups", "logs:GetLogGroupFields", "logs:StartQuery", "logs:StopQuery", "logs:GetQueryResults", "logs:GetLogEvents" ], "Resource": "*" }, { "Sid": "AllowReadingTagsInstancesRegionsFromEC2", "Effect": "Allow", "Action": ["ec2:DescribeTags", "ec2:DescribeInstances", "ec2:DescribeRegions"], "Resource": "*" }, { "Sid": "AllowReadingResourcesForTags", "Effect": "Allow", "Action": "tag:GetResources", "Resource": "*" } ]}Metrics and Logs:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AllowReadingMetricsFromCloudWatch", "Effect": "Allow", "Action": [ "cloudwatch:DescribeAlarmsForMetric", "cloudwatch:DescribeAlarmHistory", "cloudwatch:DescribeAlarms", "cloudwatch:ListMetrics", "cloudwatch:GetMetricData", "cloudwatch:GetInsightRuleReport" ], "Resource": "*" }, { "Sid": "AllowReadingLogsFromCloudWatch", "Effect": "Allow", "Action": [ "logs:DescribeLogGroups", "logs:GetLogGroupFields", "logs:StartQuery", "logs:StopQuery", "logs:GetQueryResults", "logs:GetLogEvents" ], "Resource": "*" }, { "Sid": "AllowReadingTagsInstancesRegionsFromEC2", "Effect": "Allow", "Action": ["ec2:DescribeTags", "ec2:DescribeInstances", "ec2:DescribeRegions"], "Resource": "*" }, { "Sid": "AllowReadingResourcesForTags", "Effect": "Allow", "Action": "tag:GetResources", "Resource": "*" } ]}跨账号可观测性:
{ "Version": "2012-10-17", "Statement": [ { "Action": ["oam:ListSinks", "oam:ListAttachedLinks"], "Effect": "Allow", "Resource": "*" } ]}AWS Cloudwatch 数据源配置示例
几种认证方式的 AWS CLoudwatch 配置示例如下:
AWS SDK(default):
apiVersion: 1datasources: - name: CloudWatch type: cloudwatch jsonData: authType: default defaultRegion: eu-west-2使用 Credentials 配置文件:
apiVersion: 1datasources: - name: CloudWatch type: cloudwatch jsonData: authType: credentials defaultRegion: eu-west-2 customMetricsNamespaces: "CWAgent,CustomNameSpace" profile: secondary使用 AK&SK:
apiVersion: 1datasources: - name: CloudWatch type: cloudwatch jsonData: authType: keys defaultRegion: eu-west-2 secureJsonData: accessKey: "" secretKey: "" 使用 AWS SDK Default 和 IAM Role 的 ARM 来 Assume:
apiVersion: 1datasources: - name: CloudWatch type: cloudwatch jsonData: authType: default assumeRoleArn: arn:aws:iam::123456789012:root defaultRegion: eu-west-2Cloudwatch 自带仪表板
Cloudwatch 自带的几个仪表板都不太好用,建议使用 monitoringartist/grafana-aws-cloudwatch-dashboards 替代。
创建告警的查询
告警需要返回 numeric 数据的查询,而 CloudWatch Logs 支持这种查询。例如,你可以通过使用 stats命令来启用告警。
这也是一个有效的查询,用于对包括文本 "Exception" 的消息发出告警:
filter @message like /Exception/ | stats count(*) as exceptionCount by bin(1h) | sort exceptionCount desc跨账户的可观察性
CloudWatch 插件使您能够跨区域账户监控应用程序并排除故障。利用跨账户的可观察性,你可以无缝地搜索、可视化和分析指标和日志,而不必担心账户的界限。
要使用这个功能,请在 AWS 控制台的 Cloudwatch 设置下,配置一个 monitoring 和 source 账户,然后按照上文所述添加必要的 IAM 权限。
关键词:
-

环球头条:Grafana 系列-统一展示-4-AWS Cloudwatch 数据源
系列文章Grafana系列文章AWSCloudwatch数据源对于AWSCloudwatch,主要在于3种不同的认证方式:AWSSDKDefault
来源: -

环球最资讯丨Linux驱动开发笔记(二):ubuntu系统从源码编译安装gcc7.3.0编译器
前言编译ubuntu驱动之前,发现使用的gcc是7 3 0,而使用apt管理和下载的都无法直接或间接安装gcc7 3 0,于
来源: -

-

环球头条:Grafana 系列-统一展示-4-AWS Cloudwatch 数据源
环球最资讯丨Linux驱动开发笔记(二):ubuntu系统从源码编译安装gcc7.3.0编译器
世界热讯:method怎么读音_method怎么读
899元 小米高端路由器7000开售:全2.5G网口、自研三频拓展
首款天玑9200+旗舰稳了!iQOO Neo 8 Pro现身谷歌支持列表|全球快讯
薄如原子的人工神经元面世:可处理光电信号 天天观速讯
奔驰提车当天出故障 要拆变速箱!博主:建议车主坐车头直播
印度一双层轮船因超载发生倾覆事故 现场视频曝光
强弱开始模糊中超竞争更加激烈-天天热文
挑战“三大框架”的解决方案 全球速递
@Accessors 注解参数-全球报道
环球热资讯!炭火炉子烤肉好吃还是电炉子烤的好吃?
GPS侧目!北斗“女神”徐颖:我们追求毫米级甚至更小的精度_观天下
当前信息:金价又“狂飙”!全球第二大金矿商CEO透露:还押注了另一金属
环球实时:梦幻联动?马斯克公开赞同李想对于自动驾驶的理念
天津出台强降雨应急处置机制:规范处置程序 明确9项环节
内生提升能力 外源拓宽渠道 险企增资发债两手齐抓 即时
北向互换通将于15日启动 多家外资行积极筹备
【速看料】一季度西安居民人均可支配收入比上年同期实际增长5.4%
iPhone 14令人失望!五星好评率暴降:苹果十年口碑瞬间崩塌
安卓最强5G Soc!联发科天玑9200+明天发:跑分一骑绝尘
天天热消息:学系统集成项目管理工程师(中项)系列19a_成本管理(上)
ob什么意思女生_ob什么意思
新裂缝不断出现 整栋楼可怕!租户砸断承重墙 1.68亿损失业主自认倒霉?
精选!多省加入封杀行列!老头乐销冠雷丁汽车申请破产:市占率曾超30% 涉嫌诈骗
iPhone销售强劲!但iPad、Mac拖后腿了 全球报资讯
第一条高铁还没搞定!“股神”巴菲特吐槽美国火车:还停留在100多年前|环球头条
深入理解 python 虚拟机:描述器实现原理与源码分析
88.函数指针
环球信息:让老人暖胃更暖心
天天即时:两倍性能提升!玩家推测PS5 Pro详细配置
史上第一次 美国要强制规定航空公司取消或者延误时现金赔偿旅客
印度一只老虎杀死花豹 但却不吃肉:原因有二
建议买SD卡!《塞尔达传说:王国之泪》容量达16.3GB
环球消息!拒绝流氓应用 Win11安卓子系统重磅升级 安全自有一套
怀卡托大学学费_怀卡托大学-全球新资讯
茂名西站_关于茂名西站的简介
冬至是国家法定假期吗_冬至是国家法定假日-每日焦点
网络基础 登录对接CAS-跨域导致的一个意想不到的Bug
土豪该有的OLED电竞装备 AOC 2K240Hz显示器6949元(0.01ms响应)
情侣吵架从8楼将萨摩耶扔下 后续来了:男主高空抛物被抓
女子车位被女邻居霸停数月:一怒之下 直接焊死_全球今日讯
全球快资讯丨古力娜扎COS《王者荣耀》貂蝉 美丽动人超越原作
传音控股:数字人系统顺利通过全部48个测试项|天天播报
谈一谈如何使用etcd中的事务以及自己的理解
Ansible快速入门(下)
@RequestParam注解参数-世界热讯
【天天播资讯】《羊了个羊》被通报:涉欺骗误导强迫用户!曾被吐槽广告多
哈尔滨拆承重墙高楼现新裂缝 专家:或能加固到原状态 成本较高
谢谢你们,让我们的延吉之行更有意义|全球速读
87.特殊用途语言特性
20天学会 java
讯息:发挥工业互联网平台立体化赋能作用!山东“数字强省”再加速
马斯克曾发出人口消失警告 日本912万65岁以上老人仍在工作 热推荐
RTX 2080S实机运行《GTA6》画面曝光: 熟悉的味道
天天头条:线下大牌:CariaKnar内衣旗舰店男士6条装内裤39.9元
搭载麒麟710A!华为nova 8 SE官方二手机上架:999元
耗时5个月:中国空间站有了新发现 当前讯息
使用 HTTP/2 加速 Node.js 应用
世界要闻:MockMVC的使用
世界头条:辽宁:延续实施社会保险费惠企减负政策
天天热推荐:“最强法务部”出手维权:安卓Switch模拟器Skyline宣布停止开发
索尼PS5 Slim/Pro详细配置曝光:性能翻番了!
特斯拉率先涨价 电动车价格战没戏了?“白色石油”碳酸锂价格重回20万/吨以上
深蹲后开始起跳!长城汽车4月销量超9.3万辆 同比大涨73% 全球视讯
担心的事情发生了!男子庆祝离婚去蹦极绳子断裂:脖子腰椎全摔断_全球快播
度小满发布2022ESG报告:践行ESG发展理念助推可持续发展_视点
vue中手动清除KeepAlive缓存|环球视讯
【世界快播报】钉钉PC端使用 Blazor WebAssembly 读取用户信息
环球视点!财报解析 | 2022年上汽扣非净利跌破百亿 上汽乘用车盈利仍承压
西藏航空回应客机机舱内出现浓烟返航:空调组件故障 安全没影响
全球速看:21金维他维生素C片60粒9.9元抄底:立减50元
杰克辣条再开直播虐猫?人民网怒批:处刑式虐猫可憎 向人类良知挑战
砸掉承重墙 全楼无家可归 损失1.6亿!最多可判刑7年
【世界聚看点】印度:所有智能手机必须标配FM收音机 默认开启
蕙兰怎么养才好_蕙兰怎么养
全球球精选!记录--极致舒适的Vue页面保活方案
世界热头条丨云图说|图解制品仓库CodeArts Artifact
国家医保局:一季度基本医疗保险基金整体运行平稳
iPhone 15 Pro Max影像升级巨大!苹果这次硬刚安卓_动态焦点
观察:显卡散热疯了!背板上装风扇、热管:实测根本没用
买特斯拉等车更省了 上海:6月30日前购买纯电动车补贴1万
中国央行连续6个月增持黄金:这是啥意思? 新动态
当前速读:女子霸占车位拒绝挪车 业主怒将车位焊上 律师:虽有不当但不违法
世界最新:肃南:按下项目建设“快进键”
读书笔记丨理解和学习事务,让你更好地融入云原生时代
第二章-Java程序的设计环境
Python第三方库安装教程、什么是第三方库_全球消息
AI来势汹汹,这份「生存计划」请查收!|世界实时
商品日报(5月8日):商品市场情绪回暖 双焦大涨超6%豆一涨超5%
《护心》雁回人物解析 《护心》雁回是好人还是坏人_当前通讯
每日消息!阿汤哥开战机为英国王送祝福:你可以当我的僚机
淘宝发布“时光机”:可查看20年消费数据 你一共花了多少钱?
赔钱卖车?福特电动车业务巨亏 卖一辆车亏40万元 微头条
摆脱依赖美国GPS!日本计划大幅强化自家准天顶导航系统:卫星从4颗增至11颗
拉萨一路口红绿灯只有3秒?“飙车”才能过 已延长至15秒
嫁入高门的女人百度云 嫁入高门的女人-天天快资讯
昇腾实战丨DVPP媒体数据处理视频解码问题案例
记一次springboot项目漏洞挖掘 全球观速讯
微资讯!科创板收盘播报:科创50指数涨0.77% 软件股显著回暖





