最新要闻
- 全球动态:一加Ace 2全球首发1.5K灵犀触控屏:120Hz刷新率、1450nit高亮度
- 每日消息!知名玩家爆料魔兽国服已签新代理:暴雪相中上海一公司
- 全球热点!土耳其再发生5.2级地震:中国卫星传回土耳其地震震中图像
- 全麦+黑麦:舌里0脂肪全麦面包14.9元2斤40片大促
- 国产版ChatGPT!百度版已成功注册ERNIE商标:最快3月开放
- 车顶维权女车主:重启战斗模式 希望今年能明确特斯拉案件结果
- 小米首款二合一笔记本!小米笔记本12.4图赏
- 每日速看!陪伴十年被撞报废!男子躲过一劫磕头跪别爱车 网友:它值得
- 环球视点!一加Ace 2普及16GB超大内存:44个应用保活
- 世界观点:首批入手三星Galaxy S23用户开机后大跌眼镜:系统吃掉60GB存储空间
- 上海网红“安福路小公主”接代言引热议:网友感叹辣眼睛的大妈无敌了
- 全球播报:13代CPU+40系GPU 笔记本和台式机区别有多大?
- 微头条丨100%纯棉 班尼路短袖99元4件包邮:13色可选
- 今日热文:ChatGPT概念全球爆火!我国人工智能相关企业超百万家
- 没法出二手“回血”了!索尼称PS VR2初期将仅推出数字版游戏
- 世界动态:89%美国大学生用写作业!揭秘爆红ChatGPT之父:应对核末日狂囤黄金、中学就出柜
广告
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
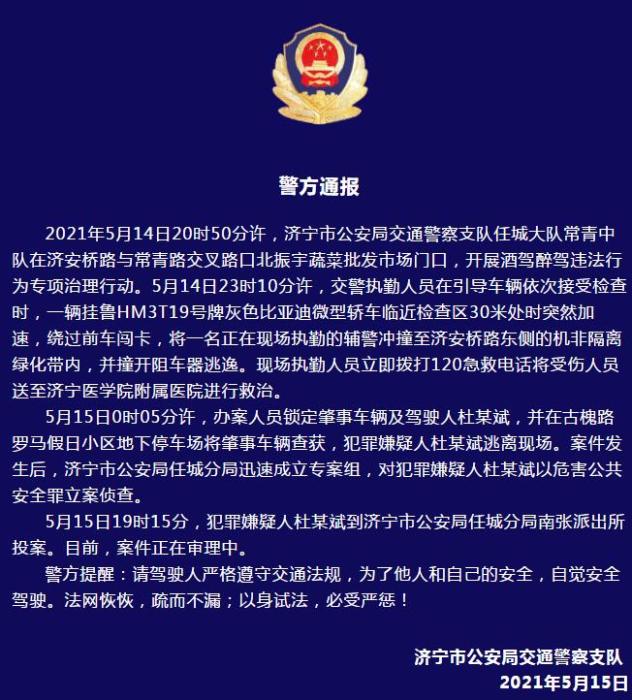
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
3.SpringSecurity+登录功能+jwt校验过滤器+redis配置
 (资料图片)
(资料图片)
SpringSecurity+登录功能+jwt校验过滤器+redis配置
一、思路分析
1.登录
①自定义登录接口 调用ProviderManager的方法进行认证 如果认证通过生成jwt把用户信息存入redis中②自定义UserDetailsService 在这个实现类中去查询数据库注意配置passwordEncoder为BCryptPasswordEncoder2.校验:
①定义Jwt认证过滤器获取token解析token获取其中的userid从redis中获取用户信息存入SecurityContextHolder二、登录接口代码实现(第一次登陆获取jwt)
1.业务代码
@Autowired private AuthenticationManager authenticationManager; @Autowired private RedisCache redisCache;@Override public ResponseResult login(User user) { //1,使用springsecurity功能认证,把用户名密码存入令牌 UsernamePasswordAuthenticationToken authenticationToken = new UsernamePasswordAuthenticationToken(user.getUserName(),user.getPassword()); //2.1,默认使用UserDetailService去内存中找user用户,需要定义Impl实现类来重写查询方法,改成从数据库查询 //2.2,UserDetailServiceImpl从数据库查询出user返回到authenticate这里。具体查看a类 Authentication authenticate = authenticationManager.authenticate(authenticationToken); //2.3,判断是否认证通过 if(Objects.isNull(authenticate)){ throw new RuntimeException("用户名或密码错误"); } //3.1,获取userid 生成token LoginUser loginUser = (LoginUser) authenticate.getPrincipal(); String userId = loginUser.getUser().getId().toString(); //3.2,生成jwt String jwt = JwtUtil.createJWT(userId); //3.3,把用户信息存入redis redisCache.setCacheObject("bloglogin:"+userId,loginUser); //4.1,把token和userinfo封装 返回 //4.2,把User转换成UserInfoVo UserInfoVo userInfoVo = BeanCopyUtils.copyBean(loginUser.getUser(), UserInfoVo.class); BlogUserLoginVo vo = new BlogUserLoginVo(jwt,userInfoVo); return ResponseResult.okResult(vo); }2.a类:UserDetailsServiceImpl
@Servicepublic class UserDetailsServiceImpl implements UserDetailsService { @Autowired private UserMapper userMapper; @Override public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException { //根据用户名查询用户信息 LambdaQueryWrapper queryWrapper = new LambdaQueryWrapper<>(); queryWrapper.eq(User::getUserName,username); User user = userMapper.selectOne(queryWrapper); //判断是否查到用户 如果没查到抛出异常 if(Objects.isNull(user)){ throw new RuntimeException("用户不存在"); } //返回用户信息 // TODO 查询权限信息封装 return new LoginUser(user); }} 3.SecurityConfig配置类
@Configurationpublic class SecurityConfig extends WebSecurityConfigurerAdapter { @Bean public PasswordEncoder passwordEncoder(){ return new BCryptPasswordEncoder(); } @Override protected void configure(HttpSecurity http) throws Exception { http //关闭csrf .csrf().disable() //不通过Session获取SecurityContext .sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS) .and() .authorizeRequests() // 对于登录接口 允许匿名访问 .antMatchers("/login").anonymous() // 除上面外的所有请求全部不需要认证即可访问 .anyRequest().permitAll(); http.logout().disable(); //允许跨域 http.cors(); } @Override @Bean public AuthenticationManager authenticationManagerBean() throws Exception { return super.authenticationManagerBean(); }}三、登录校验过滤器代码实现(校验jwt)
1.登录校验过滤器
@Componentpublic class JwtAuthenticationTokenFilter extends OncePerRequestFilter { @Autowired private RedisCache redisCache; @Override protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException, IOException, ServletException { //1,获取请求头中的token String token = request.getHeader("token"); if(!StringUtils.hasText(token)){ //说明该接口不需要登录直接放行,如果是第一次登陆的话跳转到登陆去获取token filterChain.doFilter(request, response); return; } //2,解析获取userid Claims claims = null; try { //String jwt = JwtUtil.createJWT(userId);jwt内容为id claims = JwtUtil.parseJWT(token); } catch (Exception e) { e.printStackTrace(); //token超时 token非法 //响应告诉前端需要重新登录 ResponseResult result = ResponseResult.errorResult(AppHttpCodeEnum.NEED_LOGIN); WebUtils.renderString(response, JSON.toJSONString(result)); return; } String userId = claims.getSubject(); //3,从redis中获取用户信息 LoginUser loginUser = redisCache.getCacheObject("bloglogin:" + userId); //如果获取不到 if(Objects.isNull(loginUser)){ //说明登录过期 提示重新登录 ResponseResult result = ResponseResult.errorResult(AppHttpCodeEnum.NEED_LOGIN); WebUtils.renderString(response, JSON.toJSONString(result)); return; } //4,存入SecurityContextHolder UsernamePasswordAuthenticationToken authenticationToken = new UsernamePasswordAuthenticationToken(loginUser,null,null); //UPToken令牌存入Security上下文的设置身份验证属性中,后面过滤器会从Security上下文这里获取用户信息 SecurityContextHolder.getContext().setAuthentication(authenticationToken); filterChain.doFilter(request, response); }}2.登录校验过滤器加入到过滤器组中
@Configurationpublic class SecurityConfig extends WebSecurityConfigurerAdapter { @Override @Bean public AuthenticationManager authenticationManagerBean() throws Exception { return super.authenticationManagerBean(); }//1,注入登录校验过滤器 @Autowired private JwtAuthenticationTokenFilter jwtAuthenticationTokenFilter; @Override protected void configure(HttpSecurity http) throws Exception { http //关闭csrf .csrf().disable() //不通过Session获取SecurityContext .sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS) .and() .authorizeRequests() // 对于登录接口 允许匿名访问 .antMatchers("/login").anonymous() //jwt过滤器测试用,如果测试没有问题吧这里删除了 .antMatchers("/link/getAllLink").authenticated() // 除上面外的所有请求全部不需要认证即可访问 .anyRequest().permitAll(); http.logout().disable(); //***2,把jwtAuthenticationTokenFilter添加到SpringSecurity的过滤器链中 http.addFilterBefore(jwtAuthenticationTokenFilter, UsernamePasswordAuthenticationFilter.class); //允许跨域 http.cors(); } @Bean public PasswordEncoder passwordEncoder(){ return new BCryptPasswordEncoder(); }}*** Redis使用FastJson序列化
package com.lwq.config;import com.alibaba.fastjson.JSON;import com.alibaba.fastjson.serializer.SerializerFeature;import com.fasterxml.jackson.databind.JavaType;import com.fasterxml.jackson.databind.ObjectMapper;import com.fasterxml.jackson.databind.type.TypeFactory;import org.springframework.data.redis.serializer.RedisSerializer;import org.springframework.data.redis.serializer.SerializationException;import com.alibaba.fastjson.parser.ParserConfig;import org.springframework.util.Assert;import java.nio.charset.Charset;/** * Redis使用FastJson序列化 * * @author sg */public class FastJsonRedisSerializer implements RedisSerializer{ public static final Charset DEFAULT_CHARSET = Charset.forName("UTF-8"); private Class clazz; static { ParserConfig.getGlobalInstance().setAutoTypeSupport(true); } public FastJsonRedisSerializer(Class clazz) { super(); this.clazz = clazz; } @Override public byte[] serialize(T t) throws SerializationException { if (t == null) { return new byte[0]; } return JSON.toJSONString(t, SerializerFeature.WriteClassName).getBytes(DEFAULT_CHARSET); } @Override public T deserialize(byte[] bytes) throws SerializationException { if (bytes == null || bytes.length <= 0) { return null; } String str = new String(bytes, DEFAULT_CHARSET); return JSON.parseObject(str, clazz); } protected JavaType getJavaType(Class clazz) { return TypeFactory.defaultInstance().constructType(clazz); }} ** RedisConfig Redis配置
package com.lwq.config;import org.springframework.context.annotation.Bean;import org.springframework.context.annotation.Configuration;import org.springframework.data.redis.connection.RedisConnectionFactory;import org.springframework.data.redis.core.RedisTemplate;import org.springframework.data.redis.serializer.StringRedisSerializer;@Configurationpublic class RedisConfig { @Bean @SuppressWarnings(value = { "unchecked", "rawtypes" }) public RedisTemplate redisTemplate(RedisConnectionFactory connectionFactory) { RedisTemplate template = new RedisTemplate<>(); template.setConnectionFactory(connectionFactory); FastJsonRedisSerializer serializer = new FastJsonRedisSerializer(Object.class); // 使用StringRedisSerializer来序列化和反序列化redis的key值 template.setKeySerializer(new StringRedisSerializer()); template.setValueSerializer(serializer); // Hash的key也采用StringRedisSerializer的序列化方式 template.setHashKeySerializer(new StringRedisSerializer()); template.setHashValueSerializer(serializer); template.afterPropertiesSet(); return template; }} -

3.SpringSecurity+登录功能+jwt校验过滤器+redis配置
SpringSecurity+登录功能+jwt校验过滤器+redis配置一、思路分析1 登录①自定义登录接口调用ProviderMan...
来源: -

-

-

3.SpringSecurity+登录功能+jwt校验过滤器+redis配置
当前消息!K8S的基础概念
今亮点!elementui中el-table表头动态筛选条件未及时更新问题解决
世界新消息丨C#高级编程2
RocketMQ Streams拓扑构建与数据处理过程
全球动态:一加Ace 2全球首发1.5K灵犀触控屏:120Hz刷新率、1450nit高亮度
每日消息!知名玩家爆料魔兽国服已签新代理:暴雪相中上海一公司
全球热点!土耳其再发生5.2级地震:中国卫星传回土耳其地震震中图像
全麦+黑麦:舌里0脂肪全麦面包14.9元2斤40片大促
国产版ChatGPT!百度版已成功注册ERNIE商标:最快3月开放
强大的word插件:不坑盒子下载安装使用图文讲解
ChatGPT横空出世,虽然会改BUG,但程序员也不用慌
天天简讯:强大的word插件,让工作更高效:不坑盒子 2023版
pandas 用户数据分析2
车顶维权女车主:重启战斗模式 希望今年能明确特斯拉案件结果
小米首款二合一笔记本!小米笔记本12.4图赏
每日速看!陪伴十年被撞报废!男子躲过一劫磕头跪别爱车 网友:它值得
环球视点!一加Ace 2普及16GB超大内存:44个应用保活
世界观点:首批入手三星Galaxy S23用户开机后大跌眼镜:系统吃掉60GB存储空间
【天天速看料】【算法训练营day41】LeetCode343. 整数拆分 LeetCode96. 不同的二叉搜索树
今日观点!亚马逊商城入门教程_编程入门自学教程_菜鸟教程-免费教程分享
天天快资讯:计算机视觉——SSD和YOLO简介
焦点热议:CTF之WEB学习路线规划
当前焦点!第一个编译器
上海网红“安福路小公主”接代言引热议:网友感叹辣眼睛的大妈无敌了
全球播报:13代CPU+40系GPU 笔记本和台式机区别有多大?
微头条丨100%纯棉 班尼路短袖99元4件包邮:13色可选
今日热文:ChatGPT概念全球爆火!我国人工智能相关企业超百万家
没法出二手“回血”了!索尼称PS VR2初期将仅推出数字版游戏
视讯!火山引擎ByteHouse助力中国地震台网中心,快速构建一站式实时数仓
实战分享 | 金融数据采集报送平台实践
观天下!我是如何用CAP和BASE两个基础理论卷死其他组员的?
环球信息:【踩坑记录】@Transactional注解回滚不生效问题
世界微资讯!开心档-软件开发入门之MongoDB 覆盖索引查询
世界动态:89%美国大学生用写作业!揭秘爆红ChatGPT之父:应对核末日狂囤黄金、中学就出柜
当前快报:2023年首次更新!微信Mac版3.7.0发布:终于支持图片文字提取
世界观察:Github、Gitee优秀的开源项目
【ChatGPT 注册】
【天天聚看点】ChatGPT让苹果急了!消息称苹果将于下周召开内部AI峰会
环球快资讯丨299元!小米对讲机2S发布:市区5公里通话 100个对讲频道
热议:4个小号给大号浇水 缴电费再退骗蚂蚁森林能量被封号!法院判了
人工智能立大功!AI筛查阿尔茨海默病准确率达75%
每日视点!19999元!尼康发布尼克尔Z 85mm f/1.2 S镜头:模特发丝根根可数
观天下!从这些爆款小游戏中,你看到了什么?
Docker容器使用 (入门到精通)
HGAME_2023_WEB_WP_WEEK3
2799限量抢!小米Civi 2潮流版预售 网友:我一男生都表示太好看
世界报道:豆瓣仅5.7分 漫威超英大片《黑豹2》国内首映 开场票房就被《流浪地球2》超越
每日速递:男子花两千元套圈 套中两台宏光汽车:本人回应只要一辆 做人留一线
国产纯电两门跑车!哪吒E实车亮相:动力暴躁
焦点!百度类ChatGPT产品“文心一言”公开:股价应声上涨13%
诺基亚800c手机上市价格是多少?诺基亚800c手机参数
breeno指令是干什么用的?breeno指令在哪里?
戴尔笔记本电脑换电池大概多少钱?戴尔笔记本电脑开机黑屏没反应怎么办?
格力空调型号在哪里查看?格力空调型号一览表匹数
美的冰箱质量怎么样?美的冰箱怎么调温度?
天天视讯!Redis的十六种应用场景
全球短讯!一款备受欢迎的用户脚本管理器插件TampermonKey-油猴脚本管理器安装与使用
越狱最后各人物的结局是什么?电视剧越狱演员表
曾志伟的身高是什么?曾志伟个人资料
12月是什么星座?描写12月你好的优美说说
取关是什么意思?取关抖音好友对方知道吗?
期中考试家长意见怎么写?期中考试后的感想作文模板
热点评!19岁中国小伙确诊老年痴呆 全球纪录又被刷新了
全球看点:土耳其大地震 多家中国上市公司称影响有限
ChatGPT教你写AI包教包会!7段对话写出识别程序 准确度最高达99.7%
每日资讯:小米Civi 2潮流限定版来了:后盖上全是粉色Hello Kitty 超萌
世界看热讯:国产ChatGPT何时能出?百度站出来了:最快3月 评分全球第一
[西湖论剑2022]Misc-机你太美
焦点资讯:抖音视频无水印下载器,抖音视频下载器,下载未开放下载权限的视频,支持批量下载,同一作者作品自动批量下载,合集下载,话题挑战视频合集下载等
世界快消息!【2023微博签到爬虫】用python爬上千条m端微博签到数据
带了一个 3 年的开发,不会循环删除 List 中的元素,心态崩了。。
环球通讯!DataX插件二次开发指南
7斤纯铜就能压制酷睿i9 为啥还要散热风扇?原因一个字:贵
新能源起大早赶晚集 吉利失去的四年
全球新消息丨魔兽等游戏国服已停服两周 暴雪高管:寻求替代方式服务中国玩家
全球热点评!法拉利2022年销量破纪录 员工年终奖人均10万
世界新动态:读Java实战(第二版)笔记03_引入和使用流
焦点快看:必知必会的设计原则——开放封闭原则
焦点信息:官方加紧备货!红魔8 Pro系列开售一个多月供不应求:网友反映“秒没”
全球要闻:2.5K触屏骁龙本!小米Book 12.4二合一首销:到手2899元
环球微动态丨2023年来最强雨雪上线:北方下雪、南方暴雨 影响超20省份
单踏板不爽、刹车失灵无妨!特斯拉83%车主为新用户 客户流失低忠诚度最高
【环球速看料】聊天机器人ChatGPT要抢搜索引擎生意 谷歌出手:竞品Bard来了
【天天新要闻】安卓之光来了!曝小米13 Ultra 4月登场:支持120倍变焦
天天时讯:售价超过2万元 苹果MR头显即将推出:搭载全新OS 未来将取代iPhone
【天天新视野】我国多地取消中考男女生长跑 800米对健康不利:专家喊话体育锻炼不能放松
关于pacemaker-Cluster-节点的维护模式的功能介绍
SpringBoot怎么自定义一个Starter
当前快报:做出《新闻联播》片头的齐东旭教授走了:中国CAD与计算机图形学痛失巨匠
环球观焦点:游客放孔明灯被拽下吹灭 景区回应:明文规定禁放禁售
【天天新视野】《分布式技术原理与算法解析》学习笔记Day03
Spring IOC官方文档学习笔记(九)之基于注解的容器配置
每个程序员必学的10个Git命令
打价格战底气十足:数据显示特斯拉单车利润是比亚迪6倍
梦回Win98!196MB内存电脑成功启动Win11:开机时间要30分钟
环球看热讯:node中的优先从缓存中加载模块与模块的加载规则
LeetCode 239 滑动窗口最大值- Python手撕最大堆
环球新资讯:vscode编译java程序出现NoSuchMethodError的解决方法
价格又卷下来了!致态TiPlus 7100固态硬盘新史低:1TB仅589元





